Treasury Sanctions Creators of 911 S5 Proxy Botnet
The U.S. Department of the Treasury today unveiled sanctions against three Chinese nationals for allegedly operating 911 S5, an online anonymity service that for many years was the easiest and cheapest way to route one’s Web traffic through malware-infected computers around the globe. KrebsOnSecurity identified one of the three men in a July 2022 investigation into 911 S5, which was massively hacked and then closed ten days later.

The 911 S5 botnet-powered proxy service, circa July 2022.
From 2015 to July 2022, 911 S5 sold access to hundreds of thousands of Microsoft Windows computers daily, as “proxies” that allowed customers to route their Internet traffic through PCs in virtually any country or city around the globe — but predominantly in the United States.
911 built its proxy network mainly by offering “free” virtual private networking (VPN) services. 911’s VPN performed largely as advertised for the user — allowing them to surf the web anonymously — but it also quietly turned the user’s computer into a traffic relay for paying 911 S5 customers.
911 S5’s reliability and extremely low prices quickly made it one of the most popular services among denizens of the cybercrime underground, and the service became almost shorthand for connecting to that “last mile” of cybercrime. Namely, the ability to route one’s malicious traffic through a computer that is geographically close to the consumer whose stolen credit card is about to be used, or whose bank account is about to be emptied.
In July 2022, KrebsOnSecurity published a deep dive into 911 S5, which found the people operating this business had a history of encouraging the installation of their proxy malware by any means available. That included paying affiliates to distribute their proxy software by secretly bundling it with other software.
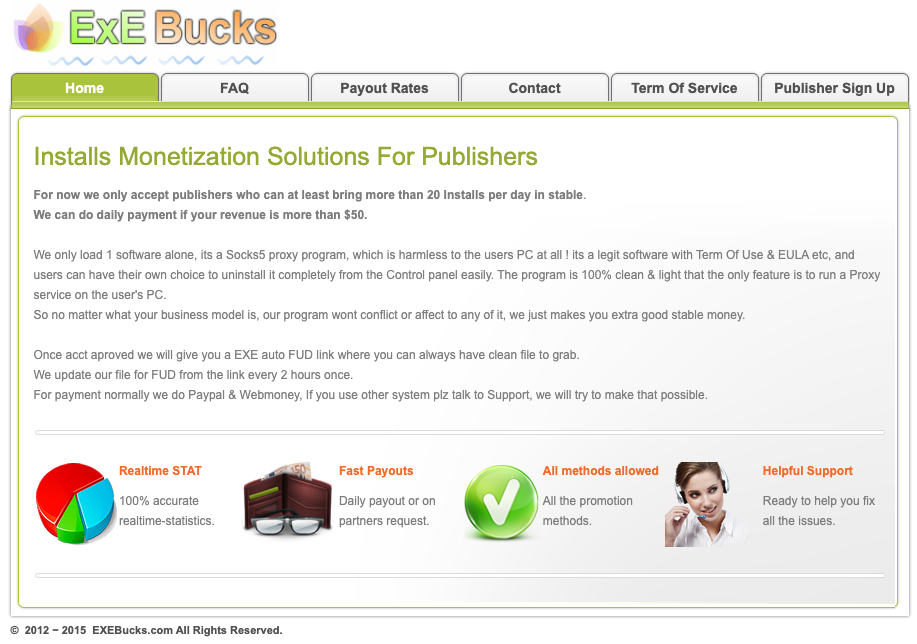
A cached copy of flashupdate dot net, a pay-per-install affiliate program that incentivized the silent installation of 911’s proxy software.
That story named Yunhe Wang from Beijing as the apparent owner or manager of the 911 S5 proxy service. In today’s Treasury action, Mr. Wang was named as the primary administrator of the botnet that powered 911 S5.
“A review of records from network infrastructure service providers known to be utilized by 911 S5 and two Virtual Private Networks (VPNs) specific to the botnet operation (MaskVPN and DewVPN) showed Yunhe Wang as the registered subscriber to those providers’ services,” reads the Treasury announcement.
Update, May 29, 12:26 p.m. ET: The U.S. Department of Justice (DOJ) just announced they have arrested Wang in connection with the 911 S5 botnet. The DOJ says 911 S5 customers have stolen billions of dollars from financial institutions, credit card issuers, and federal lending programs.
“911 S5 customers allegedly targeted certain pandemic relief programs,” a DOJ statement on the arrest reads. “For example, the United States estimates that 560,000 fraudulent unemployment insurance claims originated from compromised IP addresses, resulting in a confirmed fraudulent loss exceeding $5.9 billion. Additionally, in evaluating suspected fraud loss to the Economic Injury Disaster Loan (EIDL) program, the United States estimates that more than 47,000 EIDL applications originated from IP addresses compromised by 911 S5. Millions of dollars more were similarly identified by financial institutions in the United States as loss originating from IP addresses compromised by 911 S5.”
The sanctions say Jingping Liu was Yunhe Wang’s co-conspirator in the laundering of criminally derived proceeds generated from 911 S5, mainly virtual currency. The government alleges the virtual currencies paid by 911 S5 users were converted into U.S. dollars using over-the-counter vendors who wired and deposited funds into bank accounts held by Liu.
“Jingping Liu assisted Yunhe Wang by laundering criminally derived proceeds through bank accounts held in her name that were then utilized to purchase luxury real estate properties for Yunhe Wang,” the document continues. “These individuals leveraged their malicious botnet technology to compromise personal devices, enabling cybercriminals to fraudulently secure economic assistance intended for those in need and to terrorize our citizens with bomb threats.”
The third man sanctioned is Yanni Zheng, a Chinese national the U.S. Treasury says acted as an attorney for Wang and his firm — Spicy Code Company Limited — and helped to launder proceeds from the business into real estate holdings. Spicy Code Company was also sanctioned, as well as Wang-controlled properties Tulip Biz Pattaya Group Company Limited, and Lily Suites Company Limited.
Ten days after the July 2022 story here on 911 S5, the proxy network abruptly closed up shop, citing a data breach that destroyed key components of its business operations.
In the months that followed, however, 911 S5 would resurrect itself under a different name: Cloud Router. That’s according to spur.us, a U.S.-based startup that tracks proxy and VPN services. In February 2024, Spur published research showing the Cloud Router operators reused many of the same components from 911 S5, making it relatively simple to draw a connection between the two.
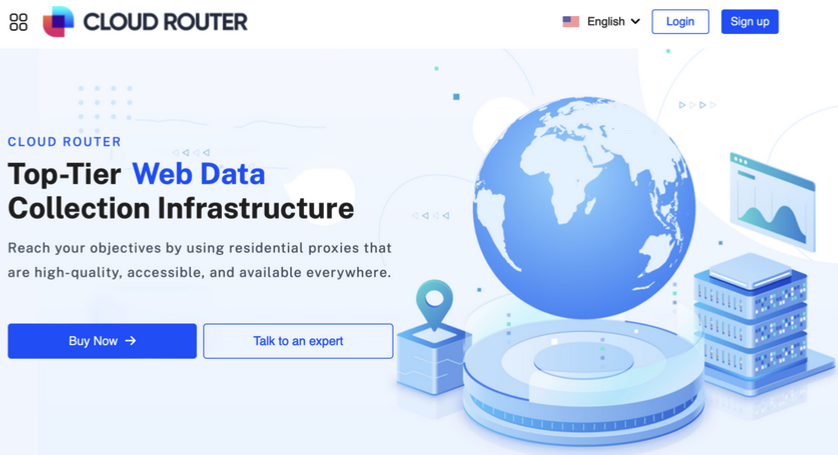
The Cloud Router homepage, which according to Spur has been unreachable since this past weekend.
Spur found that Cloud Router was being powered by a new VPN service called PaladinVPN, which made it much more explicit to users that their Internet connections were going to be used to relay traffic for others. At the time, Spur found Cloud Router had more than 140,000 Internet addresses for rent.
Spur co-founder Riley Kilmer said Cloud Router appears to have suspended or ceased operations sometime this past weekend. Kilmer said the number of proxies advertised by the service had been trending downwards quite recently before the website suddenly went offline.
Cloud Router’s homepage is currently populated by a message from Cloudflare saying the site’s domain name servers are pointing to a “prohibited IP.”