Researchers Uncover RAT-Dropping npm Package Targeting Gulp Users



The Spanish National Police dismantled a network that illicitly distributed audiovisual content, earning over 5,300,000 euros since 2015. The police arrested eight individuals in Las Palmas de Gran Canaria, Madrid, Oviedo, and Málaga, and searched two homes. The police also blocked 16 IPTV content distribution websites. According to the announcement, the investigation began in November 2022, following a complaint by the Alliance for Creativity and Entertainment against those responsible for two websites allegedly marketing videographic content that violated intellectual property rights.
The international criminal organization was using advanced technology to capture and decrypt satellite signals to distribute over 130 international TV channels and thousands of movies and series illegally. The illicitly distributed the content to over 14,000 subscribers. The authorities arrested the key members of the organization and seized two computers, a vehicle, and 80,000 euros in bank accounts. The police identified servers used by the gang and blocked 16 web pages, redirecting users to a National Police website informing them of the law enforcement operation.
“This international criminal organization used the latest technology and the most advanced technical devices to capture signals emitted via satellite in many countries. They subsequently amplified them and decrypted the multimedia content they transported, content that they then distributed publicly and illegally.” reads the press release published by the Spanish Police. “In total, more than 130 international television channels and thousands of movies and series that they made available to citizens around the world, a service for which they charged each of their more than 14,000 subscribers between 10 and 19 euros per month, or between 90 and 169 euros per year – depending on the type of subscription -, with the consequent damage to the rights of the authors, producers and distributors of these artistic works.”
The Alliance for Creativity and Entertainment (ACE), the world’s leading anti-piracy coalition, applauded the Spanish National Police for the operation against the large-scale illegal IPTV service TVMucho (also known as Teeveeing). This is the first criminal action in Spain against an operation of this size and scope.
TVMucho/Teeveeing had more than 4 million visits in 2023 and offered more than 125 channels, including major networks like BBC, ITV, Sky, and RTL.
“We commend the Spanish National Police for protecting the intellectual property rights of dozens of ACE members through this successful raid,” said Karyn Temple, Senior Executive Vice President and Global General Counsel for the Motion Picture Association (MPA). “The operation reinforces ACE’s commitment to partnering with regional authorities in identifying and confronting digital copyright infringement. We look forward to continuing our joint mission to protect the creative economy in Spain and beyond.”
Let me remind you that also subscribers to illegal streaming services could be investigated and fined by law enforcement.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Spanish police)


Researchers at Insikt Group observed Russian GRU’s unit APT28 targeting networks across Europe with information-stealer Headlace and credential-harvesting web pages. The experts observed the APT deploying Headlace in three distinct phases from April to December 2023, respectively, using phishing, compromised internet services, and living off the land binaries. The credential harvesting pages were designed to target Ukraine’s Ministry of Defence, European transportation infrastructures, and an Azerbaijani think tank. The credential harvesting pages created by the group can defeat two-factor authentication and CAPTCHA challenges by relaying requests between legitimate services and compromised Ubiquiti routers.
In some attackers, threat actors created specially-crafted web pages on Mocky that interact with a Python script running on compromised Ubiquiti routers to exfiltrate the provided credentials.
The compromise of networks associated with Ukraine’s Ministry of Defence and European railway systems could allow attackers to gather intelligence to influence battlefield tactics and broader military strategies. Additionally, their interest in the Azerbaijan Center for Economic and Social Development indicates a potential agenda to understand and possibly influence regional policies.
Insikt Group speculates the operation is aimed at influencing regional and military dynamics.
The APT28 group (aka Fancy Bear, Pawn Storm, Sofacy Group, Sednit, BlueDelta, and STRONTIUM) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. The group was involved also in the string of attacks that targeted 2016 Presidential election.
The group operates out of military unity 26165 of the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS).
The attack chain used in the attacks detailed by Insikt Group has seven distinct infrastructure stages to filter out sandboxes, incompatible operating systems, and non-targeted countries. Victims who failed these checks downloaded a benign file and were redirected to Microsoft’s web portal, msn.com. Those who passed the checks downloaded a malicious Windows BAT script, which connected to a free API service to execute successive shell commands.

In December 2023, researchers from Proofpoint and IBM detailed a new wave of APT spear-phishing attacks relying on multiple lure content to deliver Headlace malware. The campaigns targeted at least thirteen separate nations.
“Upon analyzing Headlace geofencing scripts and countries targeted by credential harvesting campaigns from 2022 onwards, Insikt Group identified that thirteen separate countries were targeted by BlueDelta. As expected, Ukraine topped the list, accounting for 40% of the activity.” reads the report published by the Insikt Group. “Türkiye might seem like an unexpected target with 10%, but it’s important to note that it was singled out only by Headlace geofencing, unlike Ukraine, Poland, and Azerbaijan, which were targeted through both Headlace geofencing and credential harvesting.”
Researchers call on organizations within government, military, defense, and related sectors, to bolster cybersecurity measures: prioritizing the detection of sophisticated phishing attempts, restricting access to non-essential internet services, and enhancing surveillance of critical network infrastructure.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Russia)

According to research conducted by Proton and Constella Intelligence, the email addresses and other sensitive information of 918 British MPs, European Parliament members, and French deputies and senators are available in the dark web marketplaces. 40% of 2,280 official government email addresses from the British, European, and French Parliaments were exposed, including passwords, birth dates, and other details.
Most leaked data email addresses belong to British MPs (68%), followed by EU MEPs (44%).
The researchers pointed out that French deputies and senators had the best security, with only 18% of searched emails in cybercrime forums and dark marketplaces.
Many of these MPs, MEPs, deputies, and senators hold senior positions, including heads of committees, government ministers, and senior opposition leaders. These politicians have access to highly sensitive information, and particularly alarming is that several of them are currently, or have previously been, members of committees tasked with overseeing and enforcing national and international digital strategies.
The presence of the emails on dark web shows that politicians used their official emails to create an account on third-party web services that suffered a data breach.
“The fact that these emails, which are publicly available on government websites, are on the dark web isn’t a security failure by itself. Nor is it evidence of a hack of the British, European, or French parliaments.” reads the report. “Instead, it shows that politicians used their official email addresses to set up accounts on third-party websites (which were later hacked or suffered a breach), putting themselves and the information they’re entrusted to keep safe needlessly at risk.”
Even more concerning is that researchers were able to match these email addresses with 697 plain text passwords. The experts notified impacted politician, they pointed out that if a politician reused one of these exposed passwords for their official email account, it could also be at risk.

It’s a miracle if British MPs were not involved in major scandals due to account takeovers, because 68% of searched email addresses were found on the dark web, including senior figures from both the government and the opposition. MPs’ email addresses were exposed a total of 2,110 times on the dark web, the researchers noticed that the most frequently targeted MP experiencing up to 30 breaches. On average, breached MPs had their details show up in 4.7 breaches.
The member of the European Parliament experienced fewer breaches compared to their British counterparts, but nearly half of the emails searched were found on the dark web. Out of 309 MEPs exposed, 92 were involved in 10 or more leaks. EU politicians had their email addresses exposed 2,311 times, along with 161 plaintext passwords. This raises concerns, as the European Parliament has increasingly become a target of state-sponsored attacks and acknowledges its lack of preparedness.
Impacted politicians have used their official email addressed to create accounts several sites, including LinkedIn, Adobe, Dropbox, Dailymotion, petition websites, news services, and even, in a small number of cases, dating websites.
“Even if a hostile takeover of one of these accounts won’t grant an attacker (or foreign government) access to state secrets, it could reveal that politician’s private communications or other sensitive data. Attackers could then use this information to phish or blackmail the politicians.” concludes the report.
“And this is the best possible scenario. If a breached politician reused a password that was exposed on the dark web on one of their official accounts (and failed to use two-factor authentication), it could let attackers into government systems. “
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, dark web)

Cloudflare researchers discovered phishing campaign conducted by a Russia-linked threat actor FlyingYeti (aka UAC-0149) targeting Ukraine. The experts published a report to describe real-time effort to disrupt and delay this threat activity.
At the beginning of Russia’s invasion of Ukraine on February 24, 2022, Ukraine implemented a moratorium on evictions and termination of utility services for unpaid debt. The moratorium ended in January 2024, leading to significant debt liability and increased financial stress for Ukrainian citizens. The FlyingYeti campaign exploited this anxiety by using debt-themed lures to trick targets into opening malicious links embedded in the messages. Upon opening the files, the PowerShell malware COOKBOX infects the target system, allowing the attackers to deploy additional payloads and gain control over the victim’s system.
The threat actors exploited the WinRAR vulnerability CVE-2023-38831 to infect targets with malware.
Cloudflare states that FlyingYeti’s tactics, techniques, and procedures (TTPs) are similar to the ones detailed by Ukraine CERT while analyzing UAC-0149 cluster.
UAC-0149 targeted Ukrainian defense entities with COOKBOX malware since at least the fall of 2023.
“The threat actor uses dynamic DNS (DDNS) for their infrastructure and leverages cloud-based platforms for hosting malicious content and for malware command and control (C2).” reads the report published by Cloudflare. “Our investigation of FlyingYeti TTPs suggests this is likely a Russia-aligned threat group. The actor appears to primarily focus on targeting Ukrainian military entities.”
Threat actors targeted users with a spoofed version of the Kyiv Komunalka communal housing site (https://www.komunalka.ua), hosted on an actor-controlled GitHub page (hxxps[:]//komunalka[.]github[.]io). Komunalka is a payment processor for utilities and other services in the Kyiv region.
FlyingYeti likely directed targets to this page via phishing emails or encrypted Signal messages. On the spoofed site, a large green button prompted users to download a document named “Рахунок.docx” (“Invoice.docx”), which instead downloaded a malicious archive titled “Заборгованість по ЖКП.rar” (“Debt for housing and utility services.rar”).

Once the RAR file is opened, the CVE-2023-38831 exploit triggers the execution of the COOKBOX malware.
The RAR archive contains multiple files, including one with the Unicode character “U+201F,” which appears as whitespace on Windows systems. This character can hide file extensions by adding excessive whitespace, making a malicious CMD file (“Рахунок на оплату.pdf[unicode character U+201F].cmd”) look like a PDF document. The archive also includes a benign PDF with the same name minus the Unicode character. Upon opening the archive, the directory name also matches the benign PDF name. This naming overlap exploits the WinRAR vulnerability CVE-2023-38831, causing the malicious CMD to execute when the target attempts to open the benign PDF.
“The CMD file contains the Flying Yeti PowerShell malware known as COOKBOX. The malware is designed to persist on a host, serving as a foothold in the infected device. Once installed, this variant of COOKBOX will make requests to the DDNS domain postdock[.]serveftp[.]com for C2, awaiting PowerShell cmdlets that the malware will subsequently run.” continues the report. “Alongside COOKBOX, several decoy documents are opened, which contain hidden tracking links using the Canary Tokens service.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, FlyingYeti)
Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.
International Press – Newsletter
Cybercrime
Into the Lion’s Den Inside the Growing Risk of Gift Card Fraud
Phishing with Cloudflare Workers: Transparent Phishing and HTML Smuggling
Christie’s Confirms Data Breach After Ransomware Group Claims Attack
Breach Forums Return to Clearnet and Dark Web Despite FBI Seizure
Treasury Sanctions a Cybercrime Network Associated with the 911 S5 Botnet
911 S5 Botnet Dismantled and Its Administrator Arrested in Coordinated International Operation
Largest ever operation against botnets hits dropper malware ecosystem
Hackers steal $305M from DMM Bitcoin crypto exchange
Ticketmaster confirms data hack which could affect 560m globally
How a Nigerian influencer, North Korean hacker and Canadian scammer committed fraud worldwide
Malware
New ATM Malware Threatens European Banking Security
Server Side Credit Card Skimmer Lodged in Obscure Plugin
Hacking
Remote Command Execution on TP-Link Archer C5400X
CVE-2024-23108: Fortinet FortiSIEM 2nd Order Command Injection Deep-Dive
Important Security Update – Stay Protected Against VPN Information Disclosure (CVE-2024-24919)
Detecting Cross-Origin Authentication Credential Stuffing Attacks
Recent ‘MFA Bombing’ Attacks Targeting Apple Users
Intelligence and Information Warfare
NATO holds first meeting of Critical Undersea Infrastructure Network
CERT-UA warns: Ukrainian finances targeted with SmokeLoader malware
How the DOJ is using a Civil War-era law to enforce corporate cybersecurity
LilacSquid: The stealthy trilogy of PurpleInk, InkBox and InkLoader
GRU’s BlueDelta Targets Key Networks in Europe with Multi-Phase Espionage Campaigns
OpenAI models used in nation-state influence campaigns, company says
Cybersecurity
Stop Using “SLA” When Discussing Vulnerabilities
How to Identify and Remove VPN Applications That Contain 911 S5 Back Doors
Multiple botnets dismantled in largest international ransomware operation ever
HUGE Google Search document leak reveals inner workings of ranking algorithm
NIST Getting Outside Help for National Vulnerability Database
Cybersecurity Education Maturity Assessment
Could the Next War Begin in Cyberspace?
OpenAI’s Altman Sidesteps Questions About Governance, Johansson at UN AI Summit
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, newsletter)
ShinyHunters, the current administrator of BreachForums, recently claimed the hack of Ticketmaster and offered for sale 1.3 TB of data, including full details of 560 million customers, for $500,000. Stolen data includes names, emails, addresses, phone numbers, ticket sales, and order details.
This week Ticketmaster owner Live Nation confirmed the data breach that compromised the data of 560 million customers.
On May 20, 2024, Live Nation Entertainment, Inc. (the “Company” or “we”) identified unauthorized activity within a third-party cloud database environment containing Company data (primarily from its Ticketmaster L.L.C. subsidiary) and launched an investigation with industry-leading forensic investigators to understand what happened. On May 27, 2024, a criminal threat actor offered what it alleged to be Company user data for sale via the dark web. We are working to mitigate risk to our users and the Company, and have notified and are cooperating with law enforcement. As appropriate, we are also notifying regulatory authorities and users with respect to unauthorized access to personal information.
As of the date of this filing, the incident has not had, and we do not believe it is reasonably likely to have, a material impact on our overall business operations or on our financial condition or results of operations. We continue to evaluate the risks and our remediation efforts are ongoing.
Threat actors had access to a third-party cloud database environment containing company data. The company discovered the intrusion on May 20, 2024, and immediately launched an investigation with industry-leading forensic investigators.
The stolen data were offered for sale on the dark web a week later.
“On May 20, 2024, Live Nation Entertainment, Inc. (the “Company” or “we”) identified unauthorized activity within a third-party cloud database environment containing Company data (primarily from its Ticketmaster L.L.C. subsidiary) and launched an investigation with industry-leading forensic investigators to understand what happened.” reads the form 8-K filing to the US Securities and Exchange Commission.
“On May 27, 2024, a criminal threat actor offered what it alleged to be Company user data for sale via the dark web.”
Live Nation notified regulatory authorities and impacted users.
Bleeping Computer reported that ShinyHunters told Hudson Rock Co-Founder Alon Gal that he breached both Santander and Ticketmaster. The threat actor revealed that the data was stolen from cloud storage company Snowflake by using credentials obtained through information-stealing malware to access a Snowflake employee’s ServiceNow account. The threat actors used to credential to exfiltrate data, including auth tokens for accessing customer accounts. The threat actor also claimed to have used this method to steal data from other companies.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, ShinyHunters)
The independent cyber threat intelligence analyst Anis Haboubi warns of a severe logging configuration flaw that could dramatically impact the financial industry.
— Anis Haboubi |₿| (@HaboubiAnis) May 31, 2024
Critical Vulnerability Threatens Global Finance
A severe logging configuration flaw could collapse finance. Sisense, ISO-certified and trusted by top financial groups, is at the center of this crisis.pic.twitter.com/Tbg2V4cQBZ
“Apache Log4j2 versions 2.0-beta7 through 2.17.0 (excluding security fix releases 2.3.2 and 2.12.4) are vulnerable to a remote code execution (RCE) attack where an attacker with permission to modify the logging configuration file can construct a malicious configuration using a JDBC Appender with a data source referencing a JNDI URI which can execute remote code. This issue is fixed by limiting JNDI data source names to the java protocol in Log4j2 versions 2.17.1, 2.12.4, and 2.3.2.” reads the advisory.
The vulnerability was discovered by Checkmarx security researcher Yaniv Nizry who reported it to Apache on December 27, 2020. The Apache Software Foundation released Log4j 2.17.1 version to address the flaw a couple of days later.
The recent breaches at Sisense and Snowflake, both ISO/IEC 27001 certified companies, highlight a critical vulnerability that still threatens the entire finance industry. Despite adhering to stringent security standards, the flaws in their infrastructure have exposed sensitive financial data to unauthorized access, potentially leading to catastrophic consequences, Haboubi told SecurityAffairs.
Why does this old flaw still threaten the Finance industry?
The critical flaw in logging configurations allows attackers with write access to exploit a JDBC Appender with a JNDI URI, enabling remote code execution. This can lead to complete system compromise, allowing attackers to execute malicious code remotely and gain unauthorized access to sensitive financial data. Sisense and Snowflake are trusted by top international financial groups.
“These companies rely on their services for critical operations, including data analytics and cloud storage. A breach in these systems can disrupt financial activities on a global scale, causing significant financial and reputational damage.” said Haboubi.
“The breaches have resulted in the exfiltration of several terabytes of customer data, including access tokens, email account passwords, and SSL certificates. This data can be exploited by attackers to gain further access to financial systems and conduct fraudulent activities. Interconnected Financial Systems: The financial industry is highly interconnected. A vulnerability in one system can lead to a domino effect, compromising other systems and services. The potential for widespread disruption makes this flaw particularly dangerous.”
The breaches have raised questions about whether Sisense and Snowflake were doing enough to protect sensitive data. The stolen data, which was apparently not encrypted while at rest, underscores the need for more robust security measures.
In conclusion, the flaws in the infrastructure of Sisense and Snowflake, combined with their extensive use in the finance sector, pose a significant threat. Immediate action is required to mitigate these vulnerabilities and protect the integrity of financial operations globally. Enhanced security measures, such as the integration of PEM key-based authentication, are crucial to prevent future breaches and ensure the safety of sensitive financial data.
— Anis Haboubi |₿| (@HaboubiAnis) May 31, 2024
4/4
It's crucial to update your logging configurations and implement robust SSH security measures immediately. Ensure all access points are secure to protect against potential exploits. Stay vigilant and secure! pic.twitter.com/yn6QLUL4zW
“It’s quite impressive. I believe the attackers breached the systems several months, or perhaps even years, ago. They likely waited for the right moment to exfiltrate the data, and Sisense only recently discovered the breach. One of the biggest issues for me is that Sisense allowed “Connecting to a Private Network with an SSH Tunnel” without a PEM key. This is what they discreetly fixed in the commit I shared with you. The attackers clearly exploited the Log4j vulnerability from the outset to gain privileged access to critical infrastructures. They then hid for months to see if they could maintain persistence” concludes the expert. “even today 30% of log4J installations are vulnerable to log4hell”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Log4j2)
The Japanese cryptocurrency exchange DMM Bitcoin announced that crooks stole 4,502.9 Bitcoin (BTC), approximately $304 million (48.2 billion yen), from the its wallets.
“
We deeply apologize for any inconvenience caused to our customers.” reads a message published by the exchange on its website. The page is currently unavailable.
The company assured that the customers’ Bitcoin (BTC) deposits will be fully guaranteed.
In response to the heist, DMM Bitcoin limited the following services:
・ Screening of new account openings
・ Processing of cryptocurrency withdrawals
・ Suspension of buying orders for spot trading (only selling orders accepted)
・ Suspension of new open positions for leveraged trading (only settlement orders accepted)
The company added that limit orders for spot trading and leveraged trading that have already been placed will not be canceled and that withdrawals of Japanese Yen may take longer than usual.
DMM Bitcoin has yet to provide details about the attack.
Cryptocurrency security firm Elliptic reported that this incident would be the eighth-largest crypto heist of all time, and the largest since the $477 million hack suffered by FTX, in November 2022. Elliptic also confirmed it has identified the wallets involved in the attack.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Bitcoin)

A notorious threat actor ShinyHunters is offering a huge trove of data allegedly stolen from the Santander Bank for sale. ShinyHunters claims to have stolen information for 30 million customers, employees, and bank account data.
In mid-May, the Spanish financial institution Santander disclosed a data breach involving a third-party provider that affected customers in Chile, Spain, and Uruguay. The bank became aware of unauthorized access to one of its databases hosted by a third-party provider.
The company announced that it immediately implemented measures to contain the incident. The company blocked the compromised access to the database and established additional fraud prevention controls to protect affected customers.
“We recently became aware of an unauthorized access to a Santander database hosted by a third-party provider.” reads the statement published by the bank. “Following an investigation, we have now confirmed that certain information relating to customers of Santander Chile, Spain and Uruguay, as well as all current and some former Santander employees of the group had been accessed. Customer data in all other Santander markets and businesses are not affected.”
The compromised database contained information on all current and some former employees.
The bank pointed out that the database did not store transactional data, online banking details, passwords, or other data that would allow someone to conduct transactions.
“No transactional data, nor any credentials that would allow transactions to take place on accounts are contained in the database, including online banking details and passwords. The bank’s operations and systems are not affected, so customers can continue to transact securely.” continues the statement.
The financial institution hasn’t provided technical details of the incident or what kind of data was exposed. It’s unclear how many individuals are impacted.
ShinyHunters is the current administrator of BreachForums, the cybercrime forum that recently resurrected two weeks after a law enforcement operation that seized its infrastructure.
ShinyHunters claimed the hack of Ticketmaster and offered for sale 1.3 TB of data, including full details of 560 million customers, for $500,000. Stolen data includes names, emails, addresses, phone numbers, ticket sales, and order details.
On May 30, 2024, ShinyHunters published an announcement titled: “Santander Bank Data – Spain, Chile, Uruguay – Customers, CC, Bank, more” that claims country affected are Spain, Chile, and Uruguay.
Data contains
The price for the data is $2M for a one-time sale.
The seller also invites Santander to buy this data.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, ShinyHunters)

Between October 25 and October 27, 2023, the Chalubo malware destroyed more than 600,000 small office/home office (SOHO) routers belonging to the same ISP.
Black Lotus did not name the impacted ISP, however, Bleeping Computer speculates the attack is linked to the Windstream outage that occurred during the same timeframe.
Chalubo (ChaCha-Lua-bot) is a Linux malware that was first spotted in late August 2018 by Sophos Labs while targeting IoT devices. Threat actors aimed at creating a botnet used to launch DDoS attacks.
The malware borrows code from the Xor.DDoS and Mirai bots, it also implements fresh evasion techniques, such as encrypting both the main component and its corresponding Lua script using the ChaCha stream cipher.
The attackers used brute-force attacks (using the root:admin credential) on SSH servers to distribute the bot.
In 2023 attacks observed by Lumen, the bot targeted ActionTec T3200s, ActionTec T3260s, and Sagemcom F5380 router models.
Public scan data confirmed that took offline 49% of all modems from the impacted ISP’s autonomous system number (ASN) during the attacks. The infections rendered the devices inoperable, and required a hardware-based replacement.
Lumen researchers speculate that the threat actors used commodity malware instead of custom tools to make attribution difficult. At the time of the report, the researchers have yet to find a link to known nation-state activity clusters. The experts believe with high confidence that the malicious firmware update was a deliberate act intended to cause an outage. The attack only impacted a single ASN.
The attack roughly damaged 179,000 ActionTec and 480,000 Sagemcom routers. Most of the infections are in the US, Brazil and China.
“Our analysis revealed that one specific ASN had a drop of roughly 49% in the number of devices exposed to the internet.” reads the analysis published by Lumen. “We compared the banner hashes that were present on this ASN on October 27, to the banner hashes present on October 28th and observed a drop of ~179k IP addresses that had an ActionTec banner. This included a drop of ~480k devices associated with Sagemcom, likely the Sagemcom F5380 as both this model and the ActionTec modems were both modems issued by the ISP.”

The researchers did not discover an exploit used for initial access, they speculate threat actor likely used weak credentials or exploited an exposed administrative interface.
The first-stage payload is a bash script (“get_scrpc”) that fetches a second script called “get_strtriiush.” get_strtriiush retrieves and executes the primary bot payload, “Chalubo” (“mips.elf”). Chalubo runs in the memory of the targeted device and wipes all files from the disk. It also changes the process name after its execution to avoid detection.
The researchers noticed that the newer version of the malware does not maintain persistence on the infected devices.
Between September and November 2023, the research discovered that there were about 45 malware panels exposed on the internet. While 28 of the panels interacted with 10 or fewer bots, the top ten panels interacted with anywhere between ~13,500 to ~117,000 unique IP addresses over a 30-day timeframe. The analysis of the telemetry associated with those IP addresses revealed that over 650K unique IP addresses had contact with at least one controller over a 30-day period ending on November 3.
95% of the bots communicated with only one control panel a circumstance that suggests the entity behind these operations had distinct silos of operations.
“The event was unprecedented due to the number of units affected – no attack that we can recall has required the replacement of over 600,000 devices. In addition, this type of attack has only ever happened once before, with AcidRain used as a precursor to an active military invasion.” concludes the report. “At this time, we do not assess this to be the work of a nation-state or state-sponsored entity. In fact, we have not observed any overlap with known destructive activity clusters; particularly those prone to destructive events such as Volt Typhoon, or SeaShell Blizzard. The second unique aspect is that this campaign was confined to a particular ASN.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Chalubo)

Cisco Talos researchers reported that a previously undocumented APT group, tracked as LilacSquid, conducted a data theft campaign since at least 2021.
The attacks targeted entities in multiple industries, including organizations in information technology and industrial sectors in the United States, organizations in the energy sector in Europe, and the pharmaceutical sector in Asia.
Threat actors were observed using the open-source remote management tool MeshAgent and a customized version of QuasarRAT malware tracked by Talos as PurpleInk.
PurpleInk is the primary implant in post-exploitation activity in attacks aimed at vulnerable application servers.
The attackers exploited
The threat actors aim to establish long-term access to compromised victims’ organizations to steal sensitive data.
The researchers pointed out that LilacSquid’s tactics, techniques, and procedures (TTPs) overlap with North Korea-linked APT groups such as Andariel and Lazarus. The Andariel APT group has been reported using MeshAgent for post-compromise access, while Lazarus extensively uses SOCKs proxy and tunneling tools along with custom malware to maintain persistence and data exfiltration. LilacSquid similarly uses SSF and other malware to create tunnels to their remote servers.
InkLoader is .NET-based loader designed to run a hardcoded executable or command. It supports persistence mechanism and was spotted deploying PurpleInk.
LilacSquid uses InkLoader in conjunction with PurpleInk when they can create and maintain remote desktop (RDP) sessions using stolen credentials. After a successful RDP login, attackers downloaded InkLoader and PurpleInk, copied to specific directories, and InkLoader is registered as a service. The service is used to launch the InkLoader, which in turn deploys PurpleInk.
PurpleInk is actively developed since 2021, it relies on a configuration file to obtain information such as the command and control (C2) server’s address and port, which is typically base64-decoded and decrypted.
PurpleInk is heavily obfuscated and versatile, the malware supports multiple RAT capabilities including:
Talos also observed the APT using a custom tool called InkBox to deploy PurpleInk prior to InkLoader.
“InkBox is a malware loader that will read from a hardcoded file path on disk and decrypt its contents. The decrypted content is another executable assembly that is then run by invoking its Entry Point within the InkBox process.” reads the analysis published by Talos.
The researchers provided Indicators of Compromise (IOCs) for the above threats on GitHub.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, APT)



The BBC disclosed a data breach that occurred on May 21. Threat actors gained access to files on a cloud-based service belonging to the British public service broadcaster.
“The BBC’s information security team has alerted us to a data security incident, in which some files containing personal information of some BBC Pension Scheme members were copied from a cloud-based storage service. The files include some Pension Scheme members’ personal information including details such as names, National Insurance numbers, dates of birth and home addresses.” reads the announcement. “The data files involved were copies and there is therefore no impact to the operations of the Scheme which continues as normal.
The incident did not impact the operation of the pension scheme portal, users can continue using it.
The incident exposed the personal information of approximately 25,000 BBC Pension Scheme members, including current and former employees.
The compromised data includes Full names, National Insurance numbers, Dates of birth, Sex, and Home addresses.
The British public service broadcaster investigated the incident with the help of external experts and have already put in place additional security measures. The experts have identified the security breach’s cause and secured it.
The company is contacting all impacted members by either email or post.
At this time, the company has no evidence that the compromised files have been misused.
“Whilst there is no specific action affected members need to take, it is always important to be alert to data and cyber security.” continues the announcement.
Members are advised to be cautious of any unsolicited communications requesting personal information or unexpected actions, including letters, calls, texts, emails, and web page referrals. The company recommends avoiding responding to, clicking on links, or downloading attachments from suspicious emails.
The company notified the UK’s Information Commissioner’s Office (ICO) and the Pensions Regulator.
BBC did not provide details about the security breach, it confirmed that investigations are ongoing, but at this stage they do not know who is behind the attack.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Known Exploited Vulnerabilities catalog)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the following vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog:
The vulnerability CVE-2024-24919 is a Quantum Gateway information disclosure issue. Threat actors exploited the flaw to gain remote firewall access and breach corporate networks.
The issue impacts CloudGuard Network, Quantum Maestro, Quantum Scalable Chassis, Quantum Security Gateways, Quantum Spark Appliances. Impacted versions are R80.20.x, R80.20SP (EOL), R80.40 (EOL), R81, R81.10, R81.10.x, and R81.20.
Early this week, the security firm warned of a surge in attacks aimed at VPN solutions.
The vulnerability CVE-2024-1086 is a Linux kernel use-after-free issue that resides in the netfilter: nf_tables component that allows an attacker to achieve local privilege escalation.
According to Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities, FCEB agencies have to address the identified vulnerabilities by the due date to protect their networks against attacks exploiting the flaws in the catalog.
Experts recommend also private organizations review the Catalog and address the vulnerabilities in their infrastructure.
CISA orders federal agencies to fix this vulnerability by June 20, 2024.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Known Exploited Vulnerabilities catalog)
Researchers from ThreatFabric discovered a macOS version of the LightSpy spyware that has been active in the wild since at least January 2024.
ThreatFabric observed threat actors using two publicly available exploits (CVE-2018-4233, CVE-2018-4404) to deliver macOS implants. The experts noticed that a portion of the CVE-2018-4404 exploit is likely borrowed from the Metasploit framework.
The macOS version of LightSpy supports 10 plugins to exfiltrate private information from devices.
LightSpy is a modular spyware that has resurfaced after several months of inactivity, the new version supports a modular framework with extensive spying capabilities.
LightSpy can steal files from multiple popular applications like Telegram, QQ, and WeChat, as well as personal documents and media stored on the device. It can also record audio and harvest a wide array of data, including browser history, WiFi connection lists, installed application details, and even images captured by the device’s camera. The malware also grants attackers access to the device’s system, enabling them to retrieve user KeyChain data, device lists, and execute shell commands, potentially gaining full control over the device.
The researchers reported that starting from January 11, 2024, several URLs containing the number “96382741” were uploaded to VirusTotal. These URLs pointed to HTML and JavaScript files published on GitHub, which were related to the CVE-2018-4233 vulnerability. The flaw resides in WebKit and impacts macOS version 10.13.3 and iOS versions before 11.4. The researchers noticed that the number “96382741” was previously used as a path name for hosting LightSpy malware files for both Android and iOS.

“The starting point threat actor group used the same approach as for iOS implant distribution: triggering WebKit vulnerability inside Safari to perform unprivileged arbitrary code execution. For macOS, attackers used CVE-2018-4233 exploit, whose source code was published on the 18th of August 2018.” reads the analysis published by ThreatFabric. “Since the vulnerability affected both iOS and macOS WebKits, both iOS and macOS implants might have been delivered in the same way for some time. The difference was in lateral local privilege escalation, which is OS-specific.”
The plugins for the macOS version are different from those for other platforms, reflecting the architecture of the target systems. Notably, the desktop version has fewer exfiltration functions compared to the mobile version.
On March 21, 2024, the panel content first appeared on VirusTotal, displayed as a web page background. The next day, the panel URL was also found on VirusTotal, it was associated with Android LightSpy. Initial analysis revealed that the panel’s code had a critical mistake: it checked for authorization only after loading all scripts, briefly displaying the authenticated view to unauthorized users.
“However, in the top right corner of the window, there was a button labeled “Remote control platform,” pointing to another panel on the same control server. Due to catastrophic misconfiguration, we were able to access this panel, and anyone could do the same by accessing the top-level panel.” continues the report. “This panel contained comprehensive information about victims, fully correlating with all the exfiltration data provided in the technical analysis section of this report.”
“It became evident that regardless of the targeted platform, the threat actor group focused on intercepting victim communications, such as messenger conversations and voice recordings. For macOS, a specialised plugin was designed for network discovery, aiming to identify devices in proximity to the victim.” concludes the report. “Despite our findings, some aspects of the LightSpy puzzle remain elusive. There is no evidence confirming the existence of implants for Linux and routers, nor is there information on how they might be delivered. However, their potential functionality is known based on panel analysis.”
The researchers also provided indicators of compromise (IoC), for this version of the spyware.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)


Law enforcement agencies in the United States and Europe today announced Operation Endgame, a coordinated action against some of the most popular cybercrime platforms for delivering ransomware and data-stealing malware. Dubbed “the largest ever operation against botnets,” the international effort is being billed as the opening salvo in an ongoing campaign targeting advanced malware “droppers” or “loaders” like IcedID, Smokeloader and Trickbot.
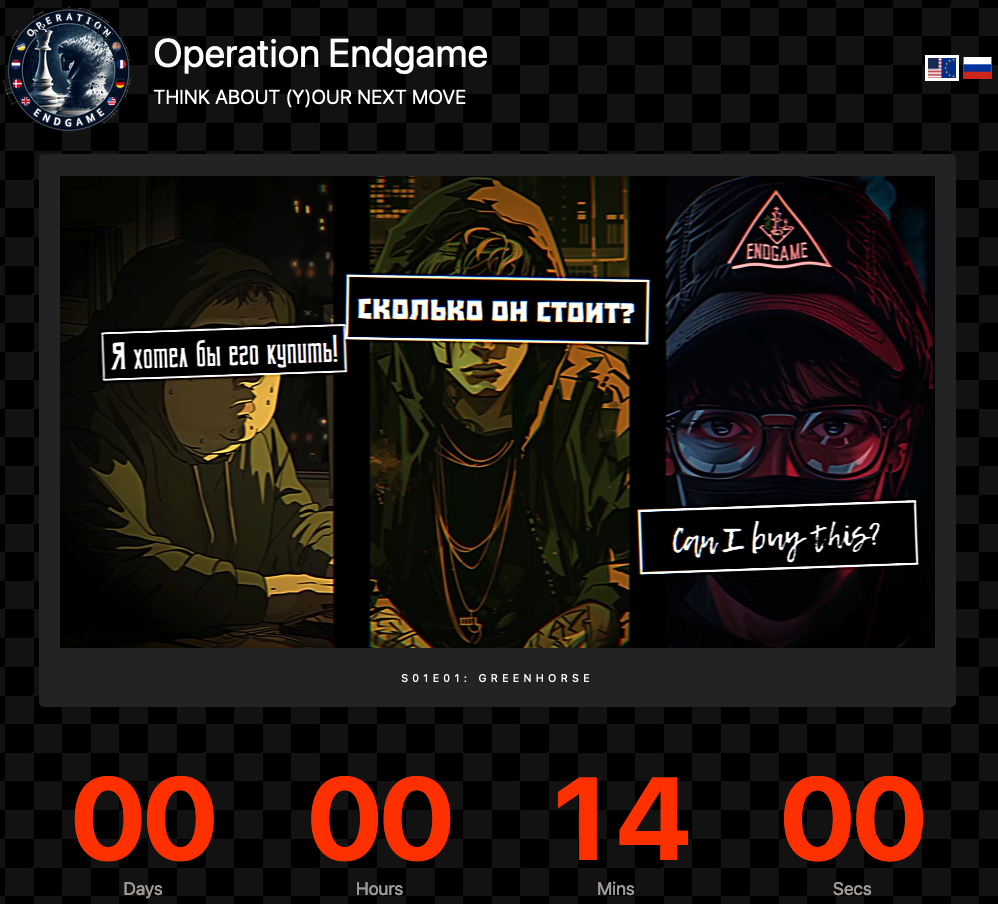
A frame from one of three animated videos released today in connection with Operation Endgame.
Operation Endgame targets the cybercrime ecosystem supporting droppers/loaders, slang terms used to describe tiny, custom-made programs designed to surreptitiously install malware onto a target system. Droppers are typically used in the initial stages of a breach, and they allow cybercriminals to bypass security measures and deploy additional harmful programs, including viruses, ransomware, or spyware.
Droppers like IcedID are most often deployed through email attachments, hacked websites, or bundled with legitimate software. For example, cybercriminals have long used paid ads on Google to trick people into installing malware disguised as popular free software, such as Microsoft Teams, Adobe Reader and Discord. In those cases, the dropper is the hidden component bundled with the legitimate software that quietly loads malware onto the user’s system.
Droppers remain such a critical, human-intensive component of nearly all major cybercrime enterprises that the most popular have turned into full-fledged cybercrime services of their own. By targeting the individuals who develop and maintain dropper services and their supporting infrastructure, authorities are hoping to disrupt multiple cybercriminal operations simultaneously.
According to a statement from the European police agency Europol, between May 27 and May 29, 2024 authorities arrested four suspects (one in Armenia and three in Ukraine), and disrupted or took down more than 100 Internet servers in Bulgaria, Canada, Germany, Lithuania, the Netherlands, Romania, Switzerland, the United Kingdom, United States and Ukraine. Authorities say they also seized more than 2,000 domain names that supported dropper infrastructure online.
In addition, Europol released information on eight fugitives suspected of involvement in dropper services and who are wanted by Germany; their names and photos were added to Europol’s “Most Wanted” list on 30 May 2024.

A “wanted” poster including the names and photos of eight suspects wanted by Germany and now on Europol’s “Most Wanted” list.
“It has been discovered through the investigations so far that one of the main suspects has earned at least EUR 69 million in cryptocurrency by renting out criminal infrastructure sites to deploy ransomware,” Europol wrote. “The suspect’s transactions are constantly being monitored and legal permission to seize these assets upon future actions has already been obtained.”
There have been numerous such coordinated malware takedown efforts in the past, and yet often the substantial amount of coordination required between law enforcement agencies and cybersecurity firms involved is not sustained after the initial disruption and/or arrests.
But a new website erected to detail today’s action — operation-endgame.com — makes the case that this time is different, and that more takedowns and arrests are coming. “Operation Endgame does not end today,” the site promises. “New actions will be announced on this website.”

A message on operation-endgame.com promises more law enforcement and disruption actions.
Perhaps in recognition that many of today’s top cybercriminals reside in countries that are effectively beyond the reach of international law enforcement, actions like Operation Endgame seem increasingly focused on mind games — i.e., trolling the hackers.
Writing in this month’s issue of Wired, Matt Burgess makes the case that Western law enforcement officials have turned to psychological measures as an added way to slow down Russian hackers and cut to the heart of the sweeping cybercrime ecosystem.
“These nascent psyops include efforts to erode the limited trust the criminals have in each other, driving subtle wedges between fragile hacker egos, and sending offenders personalized messages showing they’re being watched,” Burgess wrote.
When authorities in the U.S. and U.K. announced in February 2024 that they’d infiltrated and seized the infrastructure used by the infamous LockBit ransomware gang, they borrowed the existing design of LockBit’s victim shaming website to link instead to press releases about the takedown, and included a countdown timer that was eventually replaced with the personal details of LockBit’s alleged leader.

The feds used the existing design on LockBit’s victim shaming website to feature press releases and free decryption tools.
The Operation Endgame website also includes a countdown timer, which serves to tease the release of several animated videos that mimic the same sort of flashy, short advertisements that established cybercriminals often produce to promote their services online. At least two of the videos include a substantial amount of text written in Russian.
The coordinated takedown comes on the heels of another law enforcement action this week against what the director of the FBI called “likely the world’s largest botnet ever.” On Wednesday U.S. Department of Justice (DOJ) announced the arrest of YunHe Wang, the alleged operator of the ten-year-old online anonymity service 911 S5. The government also seized 911 S5’s domains and online infrastructure, which allegedly turned computers running various “free VPN” products into Internet traffic relays that facilitated billions of dollars in online fraud and cybercrime.