Avast Q1/2024 Threat Report
Nearly 90% of Threats Blocked are Social Engineering, Revealing a Huge Surge of Scams, and Discovery of the Lazarus APT Campaign
Foreword
We’re pleased to present the latest edition of our report for the first quarter of 2024, which has been nothing short of eventful. Here are some highlights.
Not all heroes wear capes. Just a few weeks ago, developer Andres Freund disrupted a covert threat operation that had been running for over two years. The threat actors, who managed to insert a backdoor into the widely used open-source compression library XZ/liblzma, were stopped just in time by Andres. While the identity of the threat actors remains unknown, the potential ramifications of their actions could have been catastrophic – they were almost able to gain access to any Linux machine running an infected distribution. This incident has raised important questions about the security of open-source code and its integration into critical systems and applications.
Social engineering attacks continue to be the largest threat across platforms and continue to increase their share of threats. In the mobile device landscape, more than 90% of all threats blocked in the last quarter originated from scams and similar threat types. This trend is mirrored on desktop platforms, with 87% of threats falling into the same categories. Scams, in particular, have seen a significant surge (61% on mobile and 23% on desktop), fueled by malvertising and the proliferation of malicious push notifications. The risk of falling victim to these attacks has nearly doubled in certain regions, such as Ukraine, highlighting the global reach and impact of these malicious activities. Moreover, scam authors are deploying increasingly sophisticated tactics, including the use of deepfake technology, AI-manipulated audio synchronization, and the hijacking of popular YouTube channels to disseminate fraudulent content, amplifying the potential for financial harm.

Dating scams also continue to surge, particularly in North America and Europe, with Central Europe emerging as a hotspot for such activity. Phishing remains a persistent threat, steadily increasing over the past six quarters. Prevalent phishing campaigns are detailed further in this report.
On the desktop front, we’ve uncovered a sophisticated APT campaign orchestrated by the Lazarus Group, targeting individuals in Asia with deceptive job offers. Furthermore, we discovered and reported to Microsoft an in-the-wild exploit within a Windows driver, subsequently utilized by a sophisticated rootkit in this campaign. Additionally, botnet activity has been a cause for concern – with notable updates observed in the Twizt botnet which now includes brute-forcing capabilities for Server Message Block (SMB) protocol credentials – and the expansion of the malicious DDosia project. Interestingly, the DDosia project faced frequent downtimes due to countermeasures taken by unidentified individuals. Furthermore, we successfully assisted Ukrainian CERT with the remediation of the DirtyMoe botnet.
The prevalence of Malware-as-a-Service (MaaS) stealers, exemplified by DarkGate and Luma, remains a significant threat. These malicious actors capitalize on every opportunity to deploy social engineering tactics to distribute malware.
Ransomware incidents also experienced a slight uptick in Q1/2024, notably marked by the LockBit ransomware making headlines for its initial takedown by law enforcement units, only to resurface shortly after. Furthermore, our researchers identified a new ransomware strain named HomuWitch and promptly responded by developing decryption tools to assist affected individuals. This effort supplements our previous creation, the Rhysida decryption tool, which continues to aid victims of Rhysida in recovering their files.
In the realm of remote access trojans (RATs), law enforcement units have successfully executed operations against notorious threats like the Warzone RAT, resulting in several arrests. This decisive action has already yielded tangible results, as evidenced by our telemetry data.
On the mobile front, we’ve witnessed several intriguing developments, including the resurgence of adware on the PlayStore, the emergence of MoqHao, a banker strain capable of auto-starting on victim devices, and the proliferation of GoldPickaxe, which attempts to steal facial recognition biometrics for fraudulent activities. Additionally, state-sponsored spyware continues to pose a threat to citizens.
Thank you for your continued trust in Avast. Stay safe and secure.
Jakub Křoustek, Malware Research Director
Methodology
This report is structured into two main sections: Desktop-related threats, where we describe our intelligence around attacks targeting the Windows, Linux, and Mac operating systems, with a specific emphasis on web-related threats, and Mobile-related threats, where we describe the attacks focusing on Android and iOS operating systems.
We use the term “risk ratio” in this report to denote the severity of specific threats. This is calculated as a monthly average of “Number of attacked users / Number of active users in a given country.” Unless stated otherwise, calculated risks are only available for countries with more than 10,000 active users per month.
A blocked attack is defined as a unique combination of the protected user and a blocked threat identifier within the specified time frame.
Featured Story: YouTube – the New Battleground for Phishing, Malvertising, and Cryptoscams
YouTube, with its 2.5 billion users, has become a trusted and significant target for malvertising. The combination of automated advertising systems and user-generated content provides a gateway for cybercriminals to bypass conventional security measures, making YouTube a potent channel for deploying phishing and malware. Notable threats on the platform include credential stealers like Lumma and Redline, phishing and scam landing pages, and malicious software disguised as legitimate software or updates. Additionally, YouTube serves as a conduit to Traffic Distribution Systems (TDS), directing users to malicious sites and supporting scams ranging from fake giveaways to investment schemes.
Our web scanning endpoints actively block thousands of HTTP requests, daily, that are redirected from YouTube as our users view content. This activity reflects a worrying trend:
- 4 millions unique users were protected against threats on YouTube in 2023
- Approx 500k unique users per month protected in Q1/2024

The rise of DeepFake videos in YouTube poses significant risks by realistically mimicking people or events, misleading viewers, and spreading disinformation. In Q1 we observed multiple compromised YouTube accounts with more than 50 million subscribers hijacked to spread Cryptoscam Deefake videos (more about this topic is described below in the Scam section).
Threat actors frequently utilize automated uploads and Search Engine Optimization (SEO) poisoning to enhance the visibility of harmful content. Additionally, fake comments are rampant, deceiving viewers, promoting dangerous links, and exploiting YouTube’s algorithms and user engagement to disseminate cyber threats.
There are numbers of ways in which YouTube can be exploited to disseminate threats. Observed basic Tactics and Procedures (TTP) on YouTube include:
- Phishing Campaigns Targeting Creators: Attackers send personalized emails to YouTube creators proposing fraudulent collaboration opportunities. Once trust is established, they send links to malware under the guise of software needed for collaboration, often leading to cookie theft or account compromise.
- Compromised Video Descriptions: Attackers upload videos with descriptions containing malicious links, masquerading as legitimate software downloads related to gaming, productivity tools, or even antivirus programs, tricking users into downloading malware
- Channel Hijacking for Spreading Threats: By gaining control of YouTube channels through phishing or malware, attackers repurpose these channels to promote various types of threats, such as cryptocurrency scams, often involving fake giveaways that require an initial deposit from viewers.
- Exploitation of Software Brands and Legitimate-Looking Domains: Attackers create websites that mimic reputable companies and offer illegitimate downloadable software, exploiting users’ trust.
- Social Engineering via Video Content: Attackers post tutorial videos or offers for cracked software, guiding users to download malware disguised as helpful tools. This tactic takes advantage of users seeking free access to otherwise paid services or software, leveraging YouTube’s search and recommendation algorithms to target potential victims.
David Jursa, Malware Researcher
Luis Corrons, Security Evangelist
Desktop-Related Threats
Advanced Persistent Threats (APTs): Lazarus Group in the Spotlight
An Advanced Persistent Threat (APT) is a type of cyberattack that is conducted by highly skilled and determined hackers who have the resources and expertise to penetrate a target’s network and maintain a long-term presence undetected.
We discovered a Lazarus Group campaign targeting specific individuals in Asia with misleading job offers. The precise intent of the campaign remains unknown, but the selective nature of these attacks indicates a focused interest in individuals possessing technical expertise. We suspect that these technically skilled individuals might have connections to companies involved in the gambling or betting industry, aligning with Lazarus Group’s financial motivations.
We believe the Lazarus Group used fabricated job offers to gain access to the personal computers of these victims who also used these devices for work purposes. It is likely that, a few days after the initial compromise, the attackers realized the victims had access to their company networks. Consequently, Lazarus employed sophisticated rootkit technologies to evade security measures and some security vendors.
This approach reflects the Lazarus Group’s historical tactics of exploiting vulnerable drivers and employing advanced rootkit techniques to disrupt security systems and maintain persistent access.
In this specific instance, Lazarus exploited a vulnerability in the standard Windows driver, appid.sys (CVE-2024-21338), to neutralize security software. Further details on this vulnerability can be found in our related blog post.
The complexity of these attack chains suggests that Lazarus devoted substantial resources to their planning and execution. Before executing the attack, Lazarus carefully prepared by deploying fileless malware and encrypting their tools directly onto the hard drives, as detailed in the blog post and as we recently presented at Black Hat Asia 2024 conference.

The careful and highly targeted choice of victims suggests that establishing some level of trust or connection was likely necessary before initiating the malware. The deployment of such a sophisticated arsenal, coupled with the exploit, highlights significant strategic foresight and resource commitment.
Luigino Camastra, Malware Researcher
Igor Morgenstern, Malware Researcher
Bots (With a Twist)
Bots are threats mainly interested in securing long-term access to devices with the aim of utilizing their resources, be it remote control, spam distribution, or denial-of-service (DoS) attacks.
To start on a lighter note, the biggest news in the botnet landscape was an unfortunate article in Swiss media outlet Aarguaer Zeitung which claimed a large-scale DDoS attack of millions of toothbrushes running Java. While the thought of a web-connected toothbrush running Java (which were also allegedly DDosing some random Swiss webpage) is really scary, it has been soon rectified as an inaccurate report and there was no such army of Pro-Russian toothbrushes, as the initial report suggested.
Now, unfortunately, onto the more serious note. On the geopolitical side of the threat landscape, Ukrainian state-owned enterprises have been significantly hit with DirtMoe. Due to our extensive research on DirtMoe, CERT-UA reached out to us to assist them with the remediation. Based on the experience from this successful remediation, an advisory on DirtyMoe was published by CERT-UA.
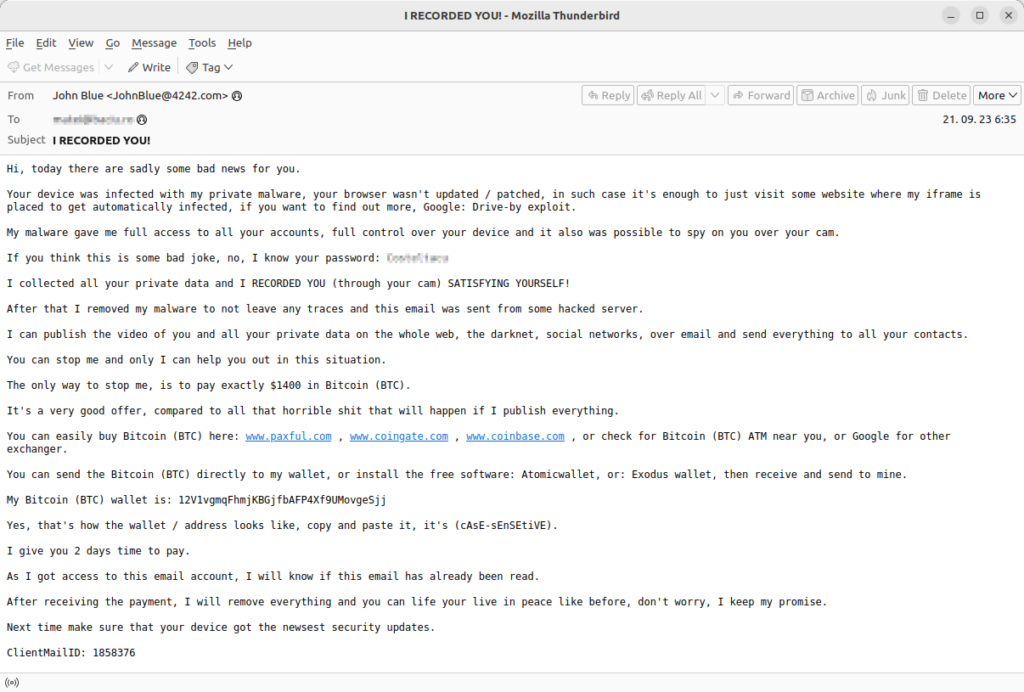
Twizt botnet has received a new module in its update providing functionality that fuels its sextortion campaign. This module relies on the common strategy of extorting the user with fake and sensitive information that was allegedly recovered from their device or account. In the case of the former, the threat actor usually refers to a device infected with RAT, in the case of the latter, the message usually contains a fake sender header and a password to give the impression that the user’s mail account has been hacked. Nevertheless, all the sent information is fabricated, and the password was quite likely taken from one of the leaked password databases that are circulating the dark web.

Last year, Twizt started bruteforcing Virtual Network Computing (VNC) credentials. At the beginning of the year, they switched to brute-forcing SMB credentials, instead. Twizt contains a hard-coded list of username/password pairs that are tried against a randomly generated target. Successful authentications are then reported to its command-and-control (C&C) server.
Our usual story on DDosia has a very surprising twist this quarter. Presumably, someone was actively targeting the DDosia C&C infrastructure, repeatedly causing outages in the proxy servers fronting real C&C servers. This resulted in rapid infrastructure changes in this outer layer, with every new proxy C&C having an approximate lifetime of 2 days before being unavailable again. Due to the absence of a client update mechanism in case of C&C outage, this forced the project owners to produce new clients every few days. Later, they started distributing new clients exclusively via private messages, presumably to reduce information exposure.

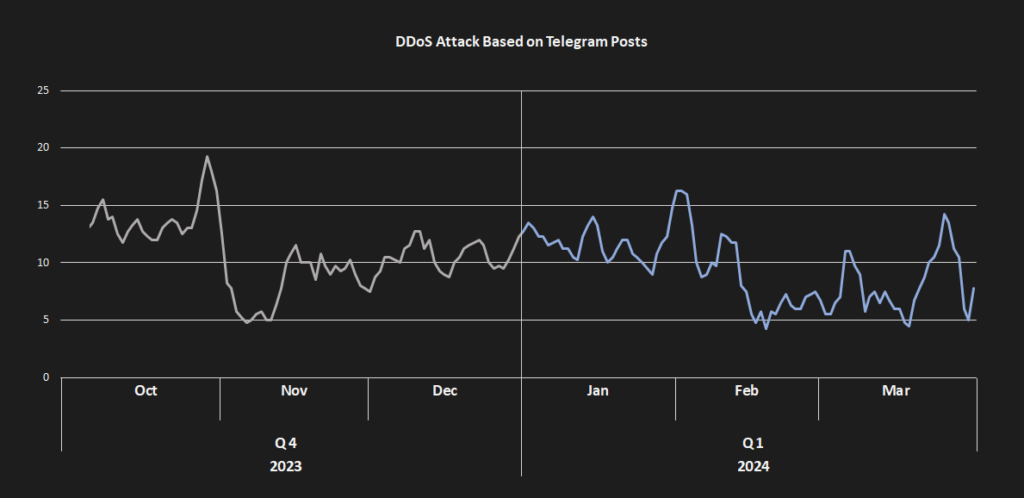
The requirement to manually update DDosia’s binary with each update along with frequent C&C outages resulted in a significant decrease in the impact of their attacks. This has prompted a heated backlash on the project’s Telegram channel where “patriotic activists” started complaining that these issues are seriously impacting their cash-flow.
This was particularly notable around February 19 when eight proxy C&Cs were shut down for five days. Even after this date, they were not able to return to their previous efficacy. The only peak during Q1/2024 is an attack at the end of March when DDosia targeted services associated with the Luxembourg government. While the number of successful targets seems to be rather high, it targeted infrastructure that was hosted on only 3 IP addresses with many subdomains. These turbulent changes were crowned by a move to a different Telegram group called “DDoSia Project” on March 7 with the original group being removed. While, up to that date, the original group was growing, ending with approximately 20,000 members, the new group started up with only around 12,000 members and soon continued in this downward trend.

While in the previous quarter DDosia was mostly focusing on banks, during the first quarter of 2024 DDosia focused mostly on various industry consortia, courts, press agencies, CERTs, and transport and logistic companies. The underlying logic stayed mostly the same – finding targets within countries that went against Russian interests.
As for the trends in the whole botnet landscape, many of the prevalent strains have stagnated. Still, we’ve seen several bigger shifts in their prevalence, including increased activity of BetaBot (13%). On the other hand, most of the other strains seem to be in decline with the following strains seeing the biggest drops: Pikabot (-48%), Tofsee (-31%), MyKings (-21%), and Dridex (-21%).

Adolf Středa, Malware Researcher
Coinminers Continue to Decline
Coinminers are programs that use a device’s hardware resources to verify cryptocurrency transactions and earn cryptocurrency as compensation. However, in the world of malware, coinminers silently hijack a victim’s computer resources to generate cryptocurrency for an attacker. Regardless of whether a coinminer is legitimate or malware, it’s important to follow our guidelines.
In the previous quarter, we observed a continued decline in the prevalence of coinminers. This downward trend persisted into Q1/2024, where the risk ratio decreased by a substantial 28%. This decrease was influenced by a slight reduction in the coinminer malware share of XMRig, which had surged in the previous quarter. However, nearly all other major coinminers actually increased in activity, thereby expanding their share.
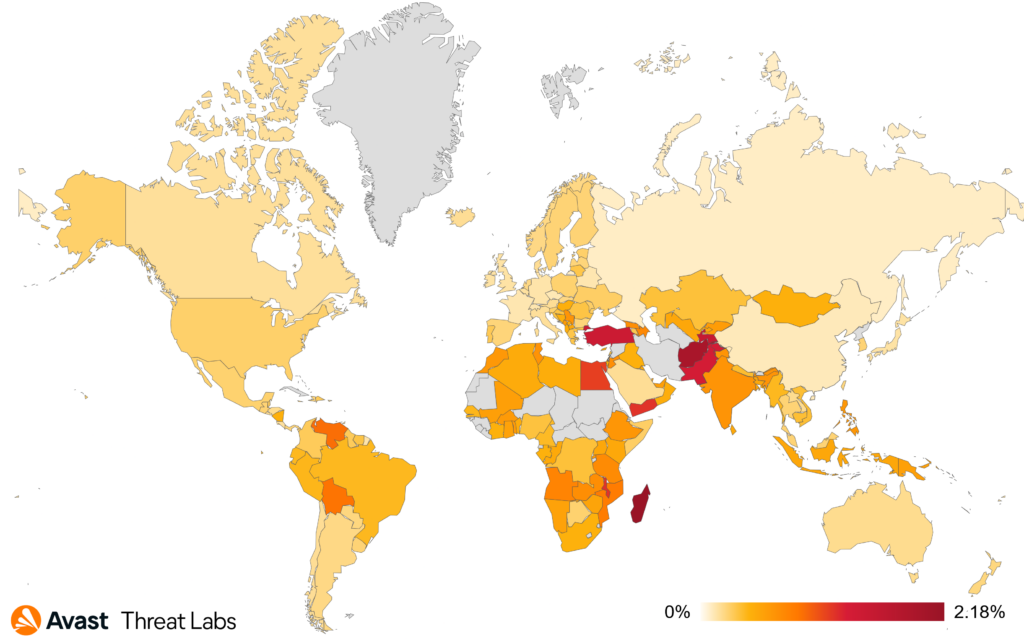
After the surge in the USA and Turkey the previous quarter, the situation calmed down a bit and we observed 39% decrease in risk ratio both countries. According to our data, more significant declines happened in India (22%), Egypt (19%), and Pakistan (13%). In total, the biggest risk of getting infected by a coinminers is still in Madagascar (2.18% risk ratio), Turkey (1.47%), Pakistan (1.35%), and Egypt (1.14%).
In the graph below, we can observe a steady decline in coinmining activities.

XMRig, the long-time most popular coinminer, decreased in coinminer malware share by 6% this quarter. Yet, it still holds 60% of the total share. All other major coinminers saw an increase in their activity, including web miners (5% increase), CoinBitMiner (24%), FakeKMSminer (37%), among others. On the other hand, SilentCryptoMiner lost 58% share this quarter.
The most common coinminers with their malware share in Q1/2024 were:
- XMRig (59.53%)
- Web miners (20.20%)
- CoinBitMiner (2.67%)
- FakeKMSminer (2.03%)
- NeoScrypt (1.75%)
- CoinHelper (1.05%)
- VMiner (0.86%)
- SilentCryptoMiner (0.84%)
Jan Rubín, Malware Researcher
Information Stealers are Still Dominated by AgentTesla
Information stealers are dedicated to stealing anything of value from the victim’s device. Typically, they focus on stored credentials, cryptocurrencies, browser sessions/cookies, browser passwords and private documents.
AgentTesla, traditionally the most prevalent information stealer we protect our users against, continued to attack users by leveraging email campaigns. One such campaign targeted Czechia, spreading the stealer via malicious attachments.

TimbreStealer, targeting almost explicitly users in Mexico, is a newcomer in the information stealers landscape. The malware is quite advanced and multi-modular, containing techniques like Heaven’s gate, among many others. It also introduces many tricks for preventing execution in sandboxes and proper debugging.
Malware-as-a-Service (MaaS) stealers continue to thrive, finding new distribution methods whenever possible. For example, DarkGate was observed to be spread via Microsoft Teams, using phishing. Furthermore, from the more technical perspective, DarkGate was exploiting Microsoft Windows SmartScreen (CVE-2024-21412).
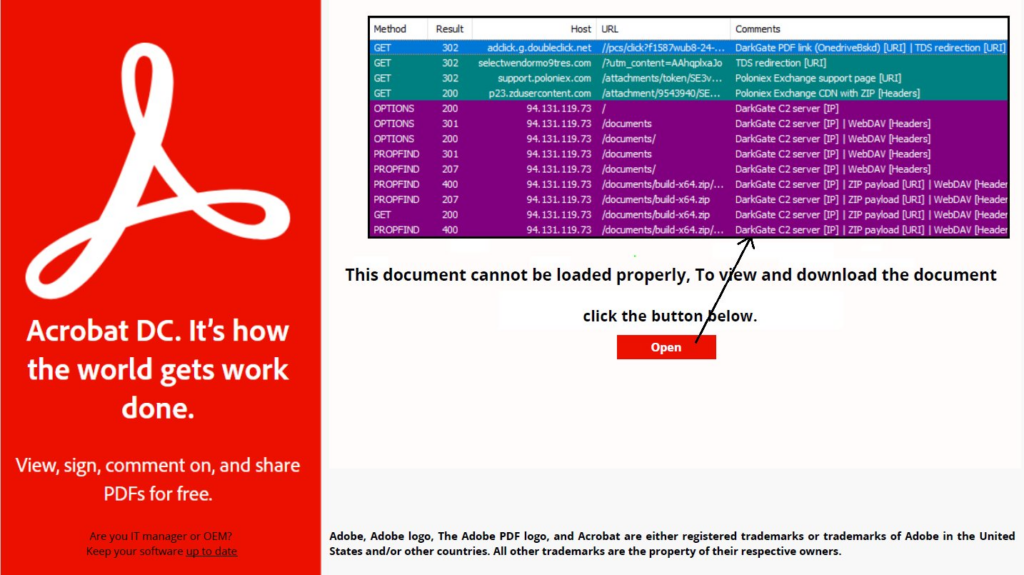
We have also observed a DarkGate campaign distributed via malicious PDF files, abusing crypto exchange and the WebDAV server. The malware delivery was done using an InternetShortcut link (.URL file), downloading the content from an opendir.
On the other hand, Lumma Stealer, which is yet another MaaS stealer, continues to spread via cracked software propagated on YouTube, using fake tutorials to mislead victims. This further emphasizes that such strains – and their creators – never miss an opportunity to leverage social engineering to distribute malware.
With regards to macOS, AtomicStealer, also known as AMOS, saw a consistent rise in occurrences on this platform during Q1/2024. This typically obfuscated malware is known for stealing passwords, cryptocurrency wallets, and cookies. It often infiltrates systems via counterfeit applications or through Google Ads poisoning. The existence of multiple generations of this threat suggests that it is likely to persist in the future, which is further underlined by its new version that was carried by a malvertising campaign in the beginning of the year.
In terms of Linux, Python information stealers were the more prevalent strains of this type with well-known malware families like Spidey, Creal, Wasp or PirateStealer. Additionally, in this quarter we uncovered a new malware strain identified as PassSniff/Putin and written in C++ that, instead of stealing the passwords from disk, steals the passwords by sniffing the HTTP traffic using both, generic rules and specific rules targeting popular services and applications.
Statistics
Overall, the global risk ratio decreased by 8% in Q1/2024 for information stealers. However, many popular stealers further increased their reach, including AgentTesla, Stealc, Fareit, and ViperSoftX.

Each of the countries where we observe the risk ratio with regards to information stealers and where we have more significant userbase thankfully experienced a decrease in activity compared to the previous quarter:
- Turkey (2.29%) with 23% Q/Q decrease
- Pakistan (2.05%) with 11% Q/Q decrease
- Egypt (1.78%) with 10% Q/Q decrease
On the other hand, we also measured increases in activity in Mexico and Czechia, following the aforementioned TimbreStealer and AgentTesla campaigns, were the risk ratio increased by 25% and 14%, respectively.
AgentTesla, the most prevalent information stealer according to our data, has increased its malware share by 17%. Its campaigns primarily target Central Europe and both North and South America. As a result, it now holds a significant 30.31% of the malware share. Notably, almost every bigger information stealer experienced an increase in activity, including Fareit (34% increase), Stealc (33%), ViperSoftX (28%), and Azorult (14%). FormBook’s share decreased by 32%, as well as Lokibot’s by 50%, balancing the scales of the overall activity of information stealers.
The most common information stealers with their malware shares in Q1/2024 were:
- AgentTesla (30.31%)
- Fareit (7.55%)
- FormBook (6.92%)
- RedLine (4.37%)
- Stealc (2.81%)
- ViperSoftX (2.28%)
- Azorult (1.93%)
- ClipBanker (1.72%)
- Raccoon (1.56%)
- Lokibot (1.41%)
- Rhadamanthys (1.36%)
Jan Rubín, Malware Researcher
David Álvarez, Malware Analyst
Ransomware: Fighting it Back
Ransomware is any type of extorting malware. The most common subtype is the one that encrypts documents, photos, videos, databases, and other files on the victim’s PC. Those files become unusable without decrypting them first. To decrypt the files, attackers demand money, “ransom”, hence the term ransomware.
The LockBit Story
In the previous threat report, we discussed new ransomware attacks. One of the top ransomware strains (or gangs, if you wish) is LockBit, which continues its encryption and extortion attacks with an undiminished intensity.
Because of the notoriety of LockBit, their – albeit brief – takedown in Q1/2024 was watched closely by the public. On February 19, operation Cronos was announced, which was a joint operation between law enforcement agencies in 10 countries. As a part of this operation, the FBI successfully breached the LockBit infrastructure, secured about 1000 private encryption keys and released a public decryptor. The following is the timeline surrounding the initiative:
- Feb 19: Operation Cronos was unveiled. LockBit leak site was replaced by a landing page from the associated law enforcement agencies:

- The main panel was replaced with a version augmented by the authorities, outing the criminality of ransomware operators:

- Feb 20: Two LockBit operators (Poland and Ukraine) were arrested, and a few other individuals were indicted for their involvement in LockBit operations
- LockBit informed all their affiliates about the breach
- For four days, there was no information about new victims of the LockBit ransomware
- Feb 24: A long message from LockBit was published by DarkWebInformer. This message explained what happened and questioned the law enforcement agencies’ success. The author of the message explains that some of his servers were running an outdated version of PHP and hence were vulnerable to CVE-2023-3824.
- Feb 25: The LockBit leak site was restored, with the FBI now shown as one of the victims. Additionally, the information about leaked data from Fulton County was re-uploaded. Note that the Fulton County Government was allegedly attacked by LockBit on Feb 14 and the leaked data was mentioned in LockBit’s message as the reason that the FBI stopped the operation instead of silently watching the servers and exfiltrating LockBit’s data increasingly, as their criminal activities continued.
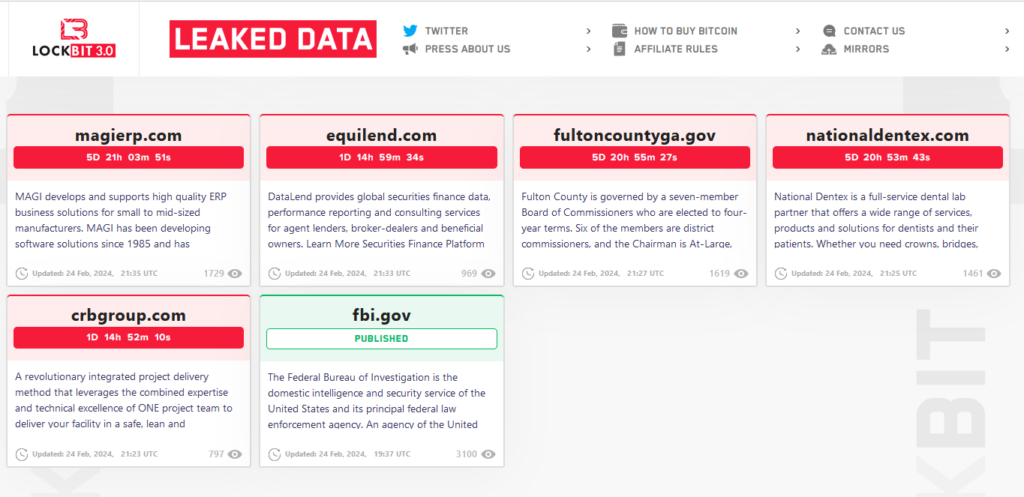
- Feb 26: LockBit operators restored their cyber-attacks and re-started attacking multiple companies daily. No, this is not a story with a happy conclusion (so far).
A tool for decrypting LockBit-encrypted data using one of 1000 seized encryption keys is. The importance of these encryption keys has been questioned by the LockBit operator himself, saying (quote) “Note that the vast majority of unprotected decryptors are from partners who encrypt brute force dedicas and spam single computers, taking $2000 ransoms” (end quote). Users attacked by LockBit ransomware may use the tool to verify if their data can be decrypted using one of the keys that were seized during the Cronos operation.
Another LockBit-related incident happened at the beginning of 2024, which demonstrates some of the ransomware operators’ modus operandi. After LockBitSupp gained access to an unspecified company, encrypted their data, and received ransom payout, he that provided access to the network.
This little incident shows what ransomware operators do to penetrate a company:
- Ransomware operator “buys an access” which means obtaining information about a company, its vulnerabilities and how to breach its network.
- Then the operator maps the company network and eventually deploys the ransomware.
- When the attacked company pays the ransom, the “access seller” gets paid for the access.
Ransomware Decryptors
As a part of the ongoing battle against ransomware, Avast released two ransomware decryptors: HomuWitch and Rhysida.
HomuWitch
HomuWitch is a ransomware that stayed under the radar since July 2023, because it targets end users with smaller ransom demands (25 – 75 USD). Searching for pirated software is the most common infection vector – instead of the desired software, users may download SmokeLoader backdoor, which later installs malicious dropper for the ransomware payload.
Unlike most ransomware strains that perform file encryption, HomuWitch also adds compression, so the encrypted files are smaller than their originals. When executed, HomuWitch searches local drives and user folders (Pictures, Downloads, Documents). All files of interest (.pdf, .doc, .docx, .ppt, .pptx, .xls, .py, .rar, .zip, .7z, .txt, .mp4, .JPG, .PNG, .HEIC, .csv) are encrypted and renamed to the .homuencrypted extension:
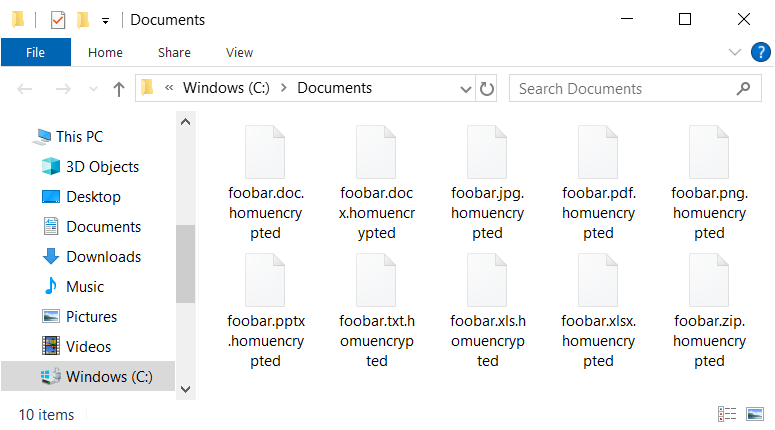
While analyzing this ransomware, we found a vulnerability that allows affected users to recover their files for free. We released free decryptor that is available on our website.
Rhysida
Rhysida is another ransomware strain defeated by the free decryption tool. This ransomware has been active since May 2023 and focuses on the enterprise sector. During summer, we discovered that this ransomware strain is decryptable without having the private RSA key, so we have been helping people who were attacked by the Rhysida ransomware.
In February 2024, Korean researchers also discovered that vulnerability and released their decryption tool publicly. It is always unfortunate to publish detailed information about the details of a vulnerability – we would like to ask fellow malware researchers not to do so and focus more on helping people affected by ransomware attacks.
Now that the details of the vulnerability are public, we also released a free decryption tool that is available both on our website and as part of the NoMoreRansom project.
Statistics
The most prevalent ransomware strains that we block in our userbase are listed below. As opposed to more popular threats like LockBit, Akira or BlackCat, you rarely read about those strains in media because – instead of attacking a large company and demanding millions of USD as ransom – these strains focus on either individual users or small businesses, and they demand ransoms that are in the thousands of dollars range.
- WannaCry (21% of ransomware share)
- Enigma (12%)
- STOP (12%)
- Mallox (aka TargetCompany) (3%)
- DarkSide (2%)
- Cryptonite (1%)
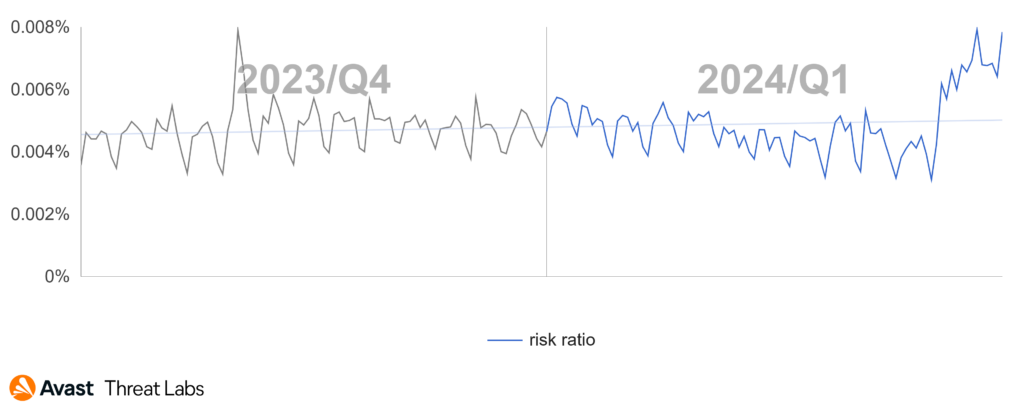
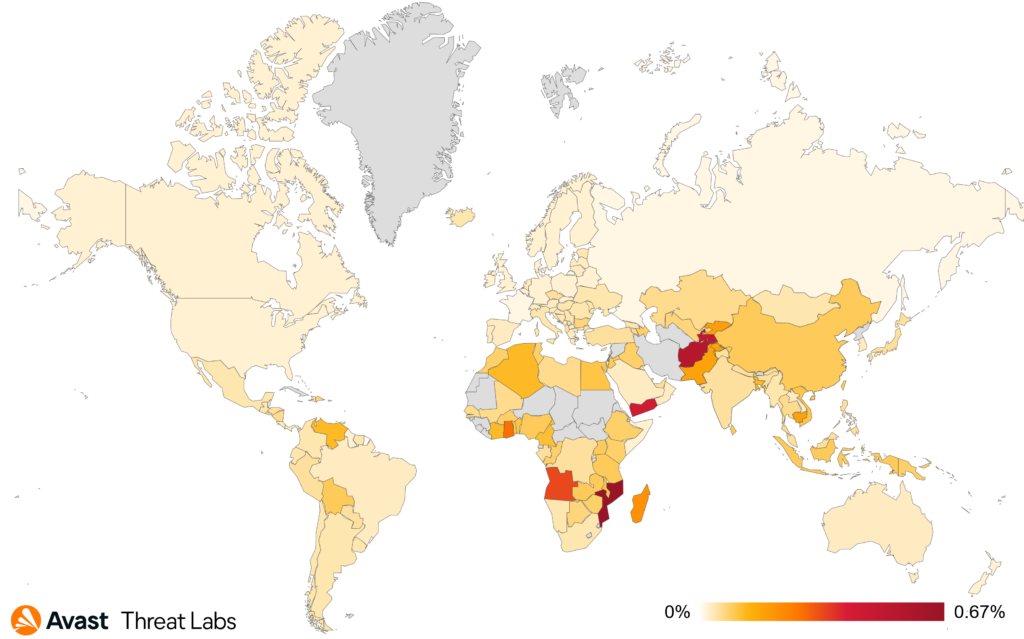
The overall ransomware risk ratio in our user base is showing an increase when compared to the previous quarter. The situation started escalating in March 2024:
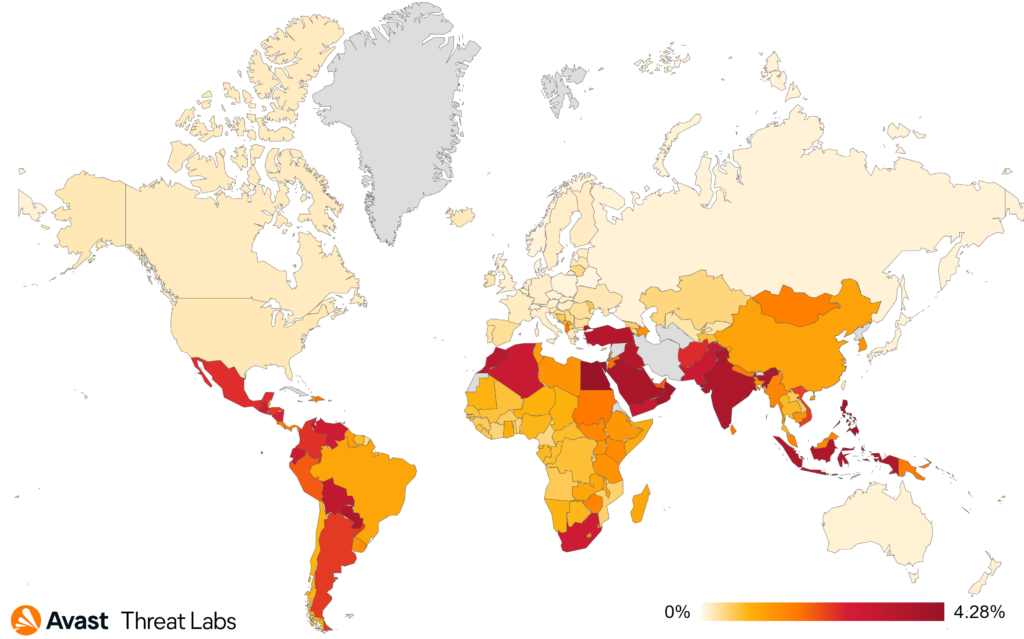
The ransomware risk ratio per country is depicted on the following map. We have noticed a significant increase in Bulgaria, Japan, Czechia, and Hungary where the risk ratio more than doubled Q/Q.
Ladislav Zezula, Malware Researcher
Jakub Křoustek, Malware Research Director
Remote Access Trojans (RATs): The End of Warzone
A Remote Access Trojan (RAT) is a type of malicious software that allows unauthorized individuals to gain remote control over a victim’s computer or device. RATs are typically spread through social engineering techniques, such as phishing emails or infected file downloads. Once installed, RATs grant the attacker complete access to the victim’s device, enabling them to execute various malicious activities, such as spying, data theft, remote surveillance, and even taking control of the victim’s webcam and microphone.
Similarly to Q1/2023 and the Netwire takedown, this year also begins with a takedown action against one of the major players in the RAT scene – the Warzone RAT was taken down at the beginning of February. According to our data, the effect was immediately visible as a sudden drop in the number of detected attacks by Warzone. Besides this takedown, it was a rather slow start to the year with only a few notable events in the RAT sphere.
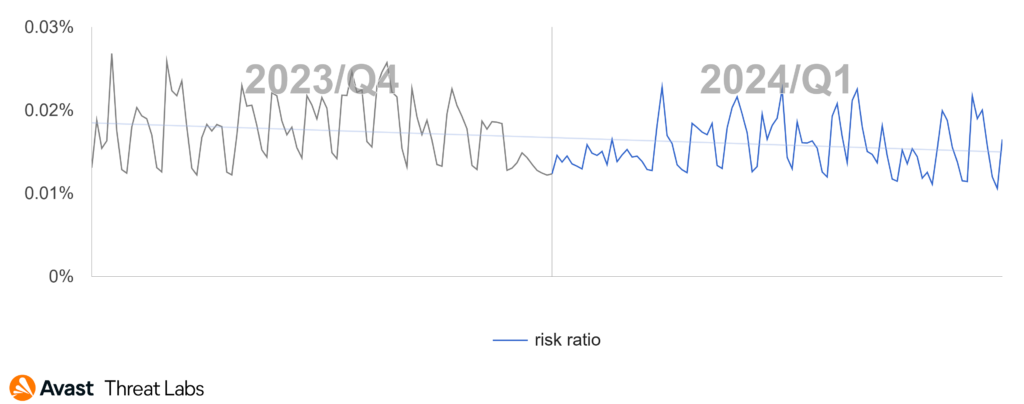
Compared to Q4/2023, the global risk ratio in the first quarter of 2024 is following a downward trend. There are several reasons for this decline. The big players Remcos, njRAT, and AsyncRat seem to have eased off a little and the number of attacks in Q1/2024 was lower than what we typically see. The takedown action against Warzone might have caused some RAT operators to halt or pause their activities. While we see increased activity of less prevalent malware strains, this isn’t enough to compensate the overall attack numbers.

The top 3 countries and RATs have not changed. We still see the highest risk ratio in Afghanistan, Iraq and Yemen, with HWorm and njRAT as the most active threats there.
The biggest increase in risk ratio was observed in Canada (+69%) due to increased activity of XWorm in February. This led to XWorm increasing its malware share by 378% which makes it the most prevalent RAT in Canada. The second highest share is in New Zealand (+33%) followed by Switzerland (+14%). Remcos was the dominant force in both countries. Despite this rise of risk ratio, Switzerland is still among the safest countries regarding RAT attacks.
The most prevalent remote access trojan strains in our userbase are as follows:
- HWorm
- Remcos
- njRAT
- AsyncRat
- QuasarRAT
- Warzone
- FlawedAmmyy
- XWorm
- NanoCore
- DarkComet
Although the overall number of detected attacks by Remcos slightly dropped, it is still very active. We recently warned about a campaign targeting most of Eastern Europe; this campaign was created in the Russian language and used a common lure “Invoice payment confirmation”.
We already mentioned XWorm in relation to Canada, however it also managed to increase its presence in most parts of the world. We also see XWorm frequently releasing new versions.
On February 7, an international operation targeted the Warzone RAT resulting in the seizure of four domains, including the primary site “warzone.ws”, and server infrastructure. One suspect was arrested in Malta and another in Nigeria. The FBI led the operation with assistance from Europol, the U.S. Department of Justice, and local law enforcement agencies. The suspects are accused of selling and advertising the RAT, providing support, and unauthorized damage to protected computers.

FortiGuard Labs also uncovered a phishing campaign spreading a new RAT, VCURMS. The campaign uses a downloader with payloads stored on public services like AWS and GitHub. There are two known payloads – the new VCURMS and STRRAT. STRRAT is also a remote access trojan which appeared in 2020. The interesting part of VCURMS is its unusual command and control channel. It communicates using emails with a Proton Mail address. Like STRRAT, VCURMS is also coded in Java. Another notable feature is its infostealer module which looks similar to RudeStealer.
Phylum and Sonatype discovered another supply chain attack in Q1/2024. Both teams found malicious packages in PyPI. These packages deploy a RAT that can also steal information from infected machines. Phylum named this threat “poweRAT”, because it relies on PowerShell in the early stages. Both reports mention the following packages as affected: pyrologin, easytimestamp, discorder, discord-dev, style.py and pythonstyles. Sonatype followed up on this story, adding several more packages to the list and showing how this threat has evolved. Communication with the C&C server happens via a Cloudflare Tunnel created from the infected machine, which means the malware does not need to modify any firewall settings. The features of RAT and information-stealing components are common on their own – however, when they combine, they create quite a dangerous threat. Phylum refers to it as a “RAT on steroids” and Sonatype as “RAT mutant”.
Ondřej Mokoš, Malware Researcher
Vulnerabilities and Exploits: An Actively Exploited Admin-to-Kernel Zero-Day
Exploits take advantage of flaws in legitimate software to perform actions that should not be allowed. They are typically categorized into remote code execution (RCE) exploits, which allow attackers to infect another machine, and local privilege escalation (LPE) exploits, which allow attackers to take more control of a partially infected machine.
In the February Patch Tuesday update, Microsoft patched CVE-2024-21338, a zero-day admin-to-kernel vulnerability discovered by Avast researchers. This zero-day was initially exploited in the wild by the Lazarus Group, who used it to enable an updated version of their FudModule data-only rootkit. This marked a significant improvement in capabilities, as previous versions of the FudModule rootkit were enabled by targeting known vulnerable drivers for BYOVD (Bring Your Own Vulnerable Driver) attacks.
Upgrading from BYOVD techniques to a zero-day in a built-in driver made the entire attack significantly stealthier, however, this wasn’t the only upgrade. Lazarus also revamped the rootkit functionality, targeting registry callbacks, object callbacks, process/thread/image callbacks, file system minifilters, Windows Filtering Platform, Event Tracing for Windows, and image verification callbacks. Additionally, the threat actors implemented a noteworthy handle table entry manipulation technique, attempting to suspend critical processes associated with Microsoft Defender, CrowdStrike Falcon, and HitmanPro. For a deeper understanding of this attack, we recommend reading our two technical blog posts or watching our Black Hat Asia 2024 talk.

In other news, the open-source world was shocked by the discovery of a backdoor in the xz/liblzma compression library. This backdoor was discovered by software engineer Andres Freund, who noticed that failing ssh logins were consuming suspicious amounts of CPU, and did the world a huge favor by deciding to investigate the root cause. The attacker(s) went by the name Jia Tan (their exact affiliation/motivation remain unclear) and demonstrated a remarkable level of patience, slowly building up trust by contributing to the open-source project for over two years. Eventually, they decided to strike and – over a number of commits – introduced the backdoor, the ultimate goal of which was to allow remote SSH logins to those with the possession of the right private key (CVE-2024-3094).
Fortunately, the backdoor was discovered relatively early, so the attackers didn’t have enough time to get the malicious code merged into major Linux distributions like Debian or Red Hat. This was a close call, however, which should be very alarming, as this could have easily been one of the biggest security incidents that we have seen in recent years. While open-source code is often regarded as more trustworthy than its closed-source counterpart, this attack demonstrates that it comes with its own challenges. Many critical open-source projects are maintained with little funding by overworked volunteers, which might unfortunately make them vulnerable to similar attacks.
Another interesting discovery was related to hyperlinks in Outlook. While Outlook would, under usual circumstances, not follow “file://” protocol links to remote resources, Haifei Li of Check Point Research discovered that just adding an extra exclamation mark (“!”) followed by some arbitrary characters might change this behavior completely. This vulnerability was assigned CVE-2024-21413 and dubbed MonikerLink, as the exclamation mark essentially turns the link into a composite moniker. When a user received an email and clicked on such a link, the remote file would be fetched and possibly parsed in the background.
Interestingly, the impact of this is twofold. First, following the link to load a resource from a remote SMB server represents yet another way to force NTLM authentication, allowing the remote server to capture NTLMv2 hashes. Second, an attacker might use this to trigger some vulnerable code, as the fetched resource might be opened in the background, attempting to look up the item moniker (the string appended after the exclamation mark). For instance, the Check Point blog demonstrated this on an RTF file, which would get opened in Microsoft Word outside protected view, representing a very sneaky 1-click vector to deliver an RTF exploit.
Jan Vojtěšek, Malware Researcher
Web Threats
The significance of web threats can be well seen not only in the numerical statistics but also in the creativity of the scammers themselves. We see scammers trying to take advantage of different trends in different groups. These cybercriminals are using the latest technology in the field of AI, or they are not afraid to invest in their fraudulent practices to improve the sophistication of their scams through other methods.
Last quarter, we reported that scams, together with phishing and malvertising, accounted for more than 75% of all threats blocked by Avast throughout the year. This quarter we have blocked over 80% for the same type of threats. This indicates a rather interesting – and very scam-ridden – start to the year.
Scams Everywhere, Including Video
A scam is a type of threat that aims to trick users into giving an attacker their personal information or money. We track diverse types of scams which are listed below.
In our Q4/2023 report, we pointed out that scam activity is increasing significantly. At that time, we saw that one of the main reasons was the high rate of malvertising campaigns. This trend has continued in Q1/2024, with the activity level from the previous peak.

Our data again shows that sites offer deals and then sending push-notifications are contributing significantly to this trend. With this in mind, we again urge everyone to always consider from which website you want to allow to send you notifications. Also remember that scammers try to disguise these offers of sending notifications as, for example, video players or as adult confirmations.
If you, unfortunately, allow access to malicious notifications, you may encounter the situation shown below.

The increasing use of malvertising and push-notifications by scammers only confirms our predictions for 2024, when we repeatedly warned that this is a global threat with huge risk potential, especially on mobile phones.
If we look at activity in specific countries, we see that Ukraine exhibited the most significant surge in risk ratio, with a concerning 97% increase (the overall risk ratio for first quarter is set at 16.51%).

Similarly, Kazakhstan and Uzbekistan displayed significant jumps in their risk ratios, +89% and +56% respectively, marking these countries as emerging hotspots for scam-related threats with overall risk ratios of 14.24% and 12.45%.
If we look further, we see interesting data for India, which also saw an increase in scam threats The current risk ratio for India is 17.26% with a quarter-over-quarter risk ratio increase of +24%.
We identified the highest scam risk ratio Georgia and Serbia in Q1/2024, with more than 30% risk ratio. In the absolute numbers, the majority of scam-targeted users were in France, Brazil, and the US.
Scam Delivery via Video
In Q1/2024 we continued to witness scam authors heavily using videos as lures in their scams. Whether video made from stock footage or an elaborate deep fake video, scammers are using all video varieties in their threats. One of the most widespread techniques involved exploiting famous individuals and significant media events to attract large audiences. As a result, scammers have devised enticing schemes that capitalize on the familiarity of well-known personalities and important world events.
An increasingly common feature of these campaigns is the use of deep fake videos, created by hijacking official videos from events and using AI to manipulate audio synchronization. These videos seamlessly blend altered audio with existing visuals, making it harder for the untrained eye to tell they’re anything but authentic. Moreover, scammers insert QR codes, leading to well-designed web pages, that promise exclusive opportunities, luring victims into further engagement.

Cryptocurrency scams of this type are particularly increasing. Once an individual moves from the video lure to the fraudulent website, they are presented with different scenarios for obtaining “beneficial” cryptocurrencies. Victims are fooled into believing that participating in these schemes will bring considerable profits. The scammers consistently promise victims the same profit margin, and victims receive the impression that – by sending any amount of cryptocurrency to specific wallets – they will receive double the amount in return. The websites even implement fake online wallet monitoring, imitating legitimate transaction activity. Additionally, these deceptive sites typically include images of well-known personalities and logos associated with authentic cryptocurrency-related companies, adding an air of legitimacy.

In Q1/2024, we observed several other incidents of abuse against famous individuals like Michael J. Saylor, Vitalik Buterin, Brad Garlinghouse, and Larry Fink.

However, the most significant cryptocurrency scam incident of the quarter was the misuse of the Starship Integrated Flight Test 3 (IFT-3). The attackers used the official SpaceX All Hands meeting video to deceive viewers and get them to visit the fraudulent websites. Moreover, the attackers have hijacked several YouTube channels, which have tens of millions of subscribers, to increase the probability of displaying a fake video in the list of recommended videos.

The preliminary analysis indicates that specific attackers’ wallets associated with these scams’ campaigns have cashflows reaching tens of thousands of dollars.
The risk ratio of this financial scam was stable in Q1/2024, but we recorded a significant peak on March 14, 2024, related to the IFT-3 event.

In terms of country distribution, the leading countries affected by the scammer group are the United States, the United Kingdom, and Germany.

Dating Scams Skyrocketing
Dating scams, also known as romance scams or online dating scams, involve fraudsters deceiving individuals into fake romantic relationships. Scammers adopt fake online identities to gain the victim’s trust, with the ultimate goal of obtaining money or enough personal information to commit identity theft.
The last quarter of last year was very interesting for dating scams, with several large campaigns witnessed through our data. In Q1/2024, we saw a significant increase since the middle of February.
What is interesting is the high activity especially in Central Europe, with countries like Hungary, Slovakia, Denmark, Austria or the Czech Republic being the most affected.
Once again, these threats are strongly supported by advertising campaigns. We often see that the sources of these advertising campaigns are sites with adult content. On such pages, the owners often try to get as much commission as possible by trying to fit advertising on their sites with almost every interaction on the page. The user is often overwhelmed with pop-ups or new window redirects, usually to dating scam sites.

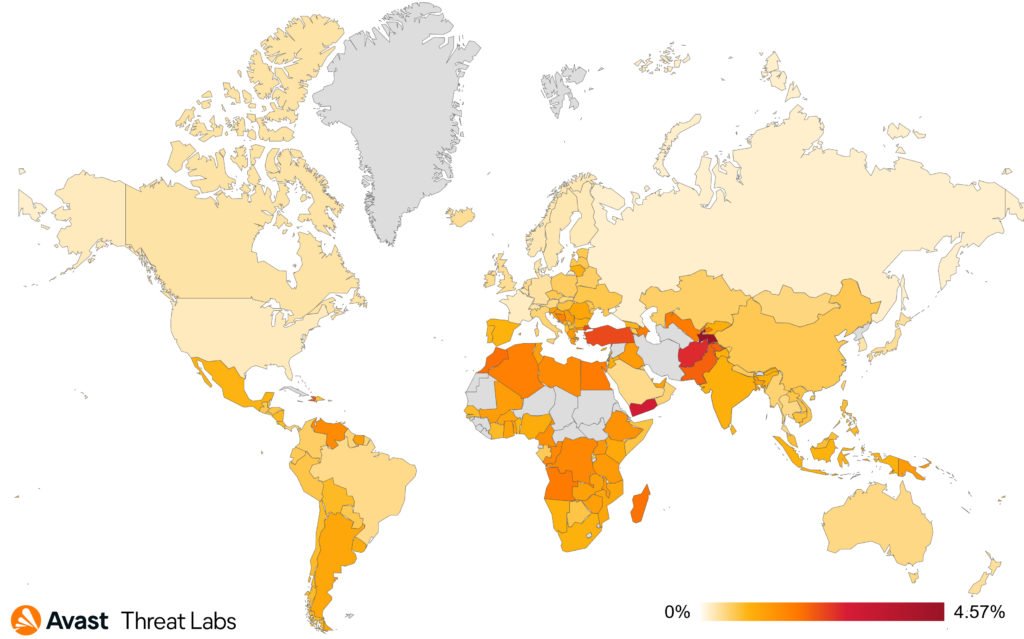
As you can see on the map, Hungary leads with the highest risk ratio rate at 5.06%. Following closely are Slovakia and Luxembourg, with risk ratios of 4.72% and 4.57% respectively.
Germany and Austria also show significant exposure to dating scams, with risk ratio rates of 4.27% and 4.10% and lastly, Czechia, with a risk ratio of 3.94%, rounds out the list.

Tech Support Scams (TSS): Steady Increase of Attacks
Tech support scam threats involve fraudsters posing as legitimate technical support representatives who attempt to gain remote access to victims’ devices or obtain sensitive personal information, such as credit card or banking details. These scams rely on confidence tricks to gain victims’ trust and often involve convincing them to pay for unnecessary services or purchase expensive gift cards. It’s important for internet users to be vigilant and to verify the credentials of anyone claiming to offer technical support services.
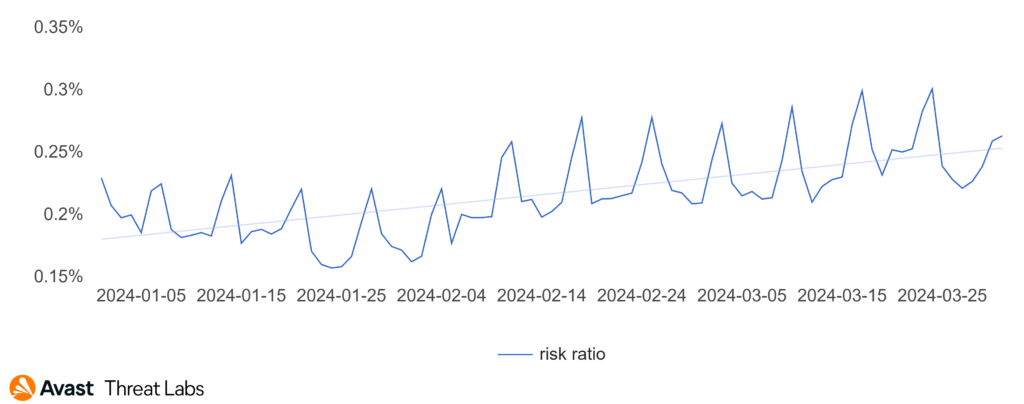
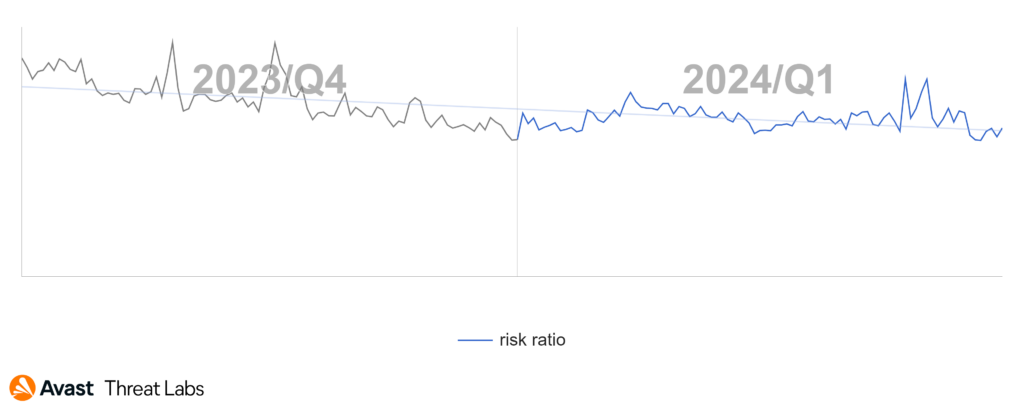
Throughout 2023, we observed a continual drop in activity related to tech support scams. In the first quarter of this year, we can say that this trend not only ended but quite the contrary – we observed an increase in tech scam activity over the quarter.

As seen on the chart above, the activity of this threat has reached the level of the beginning of Q4/2023.
Looking at the data of the full quarter, a clear increase trend is visible.

Switzerland experienced the most dramatic surge, with a 177% increase in TSS activity—the highest observed this quarter. Austria also saw a significant rise, with a 101% increase. Germany’s increase, though lower, was still notable at 65%. Additionally, Japan, traditionally a hotspot for TSS, reported a significant increase of 153%.
These escalating figures, especially notable in Europe’s wealthier nations, highlight a growing trend in cybersecurity threats in these regions.

Refund and Invoice Scams: iCloud Data Deletion Scam
Invoice scams involve fraudsters sending false bills or invoices for goods or services that were never ordered or received. Scammers rely on invoices looking legitimate, often using company logos or other branding to trick unsuspecting victims into making payments. These scams can be especially effective when targeted at businesses, as employees may assume that a colleague made the purchase or simply overlook the details of the invoice. It’s important to carefully review all invoices and bills before making any payments and to verify the legitimacy of the sender if there are any suspicions of fraud.
One of the refund and invoice scams that caught our attention in Q1/2024 targeted a top-tier service, serving as a gateway to other less valuable ones, in our assessment. The targeted account was iCloud, accompanied by a TinyURL link to a payment gateway that extracts user information, including sensitive details. iCloud is undoubtedly one of the most vital accounts to protect by enabling multi-factor authentication in order to prevent malicious actors from stealing sensitive information. According to 9to5 Google, enabling multi-factor authentication for Google users led to a 50% decrease in compromised accounts.
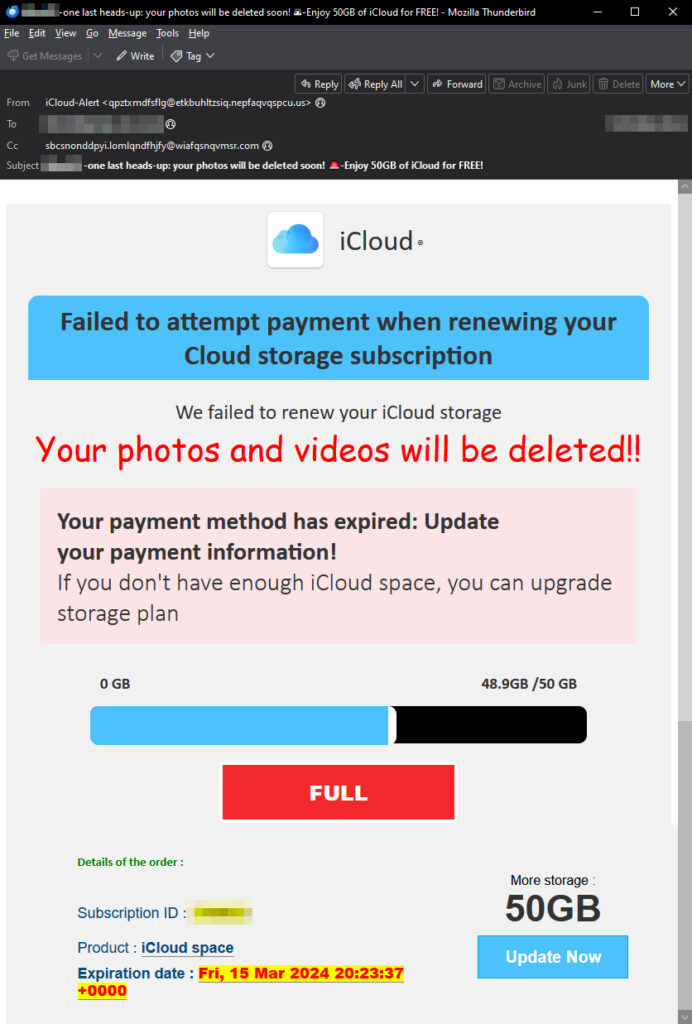
We will delve into the campaign itself which begins with a malicious email, which may evoke early 90’s nostalgia because the attackers’ Comic Sans font choice. The aim of the email is to visually intimidate, highlighting the issue at hand: your beloved photos will be deleted unless you proceed to the fake payment gateway. As always, the loading bar creates a sense of urgency, while a missed payment statement compounds the pressure. A big red button labeled “FULL” completes the sense of urgency, signaling that immediate action is required.
The email seemingly contains additional product and technical information to make it look authentic, all of which is fabricated. These include product IDs, expiration dates, and buttons for more storage. The only legitimate piece of the email is the unauthorized use of the actual iCloud logo. The subject of the email is also intriguing: we’re seeing that more cybercriminals aim to catch your attention with email subject lines using emoticons, as you see in the email sample below.
In terms of global prevalence, we can see that the English-speaking world is the most affected, along with the European Union. The countries that experienced the biggest spike in the last quarter are Belgium, up by 29%, the United Kingdom, up by 13%, and Luxembourg, up by 10%. On the other side of the spectrum, we have Australia, which experienced the largest drop, down by 29%, the United States, down by 15%, and Canada, down by 5%.
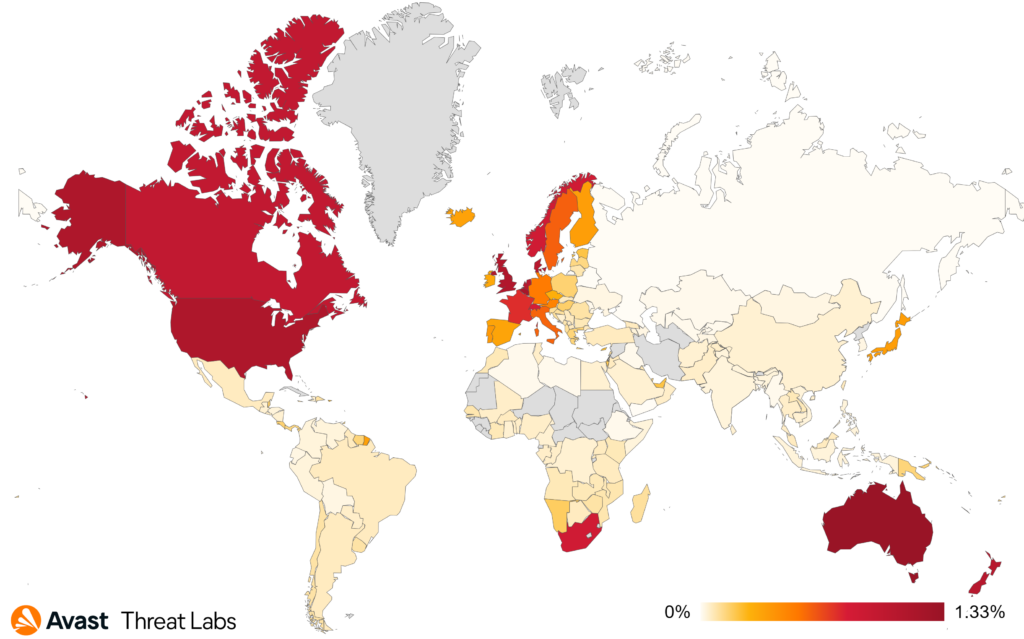
The graph showing risk ratio over time exhibits less volatility compared to the previous period. In Q1/2024, the risk did not significantly change over time and rose slightly by the end of the quarter. We can observe that the threat is still widely spread around the globe, and we anticipate seeing even more of these attacks in the future.
Phishing: Reaching New Hights
Phishing is a type of online scam where fraudsters attempt to obtain sensitive information including passwords or credit card details by posing as a trustworthy entity in an electronic communication, such as an email, text message, or instant message. The fraudulent message usually contains a link to a fake website that looks like the real one, where the victim is asked to enter their sensitive information.
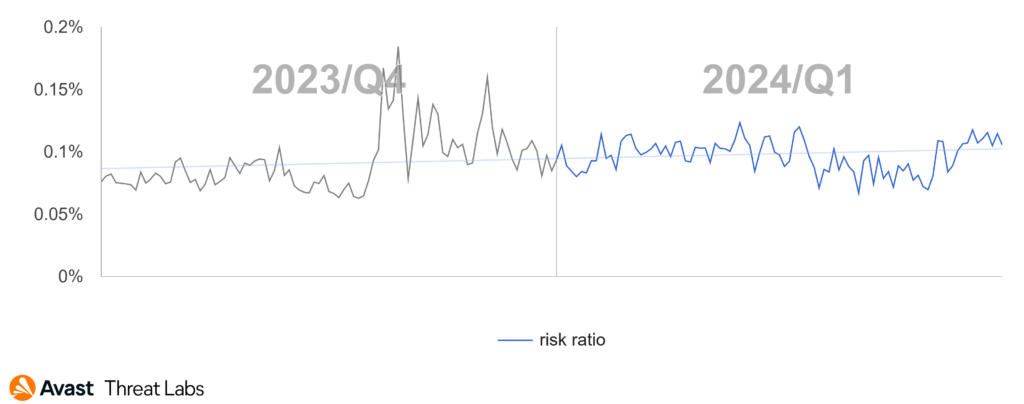
And now we come to the final, and most classic, category under web threats: Phishing. Like nearly all web threats, this category saw an increase in activity in Q1/2024, continuing the increase trend that we’ve witnessed over the last four quarter.

We’ve also observed that attackers are continuing to make heavy use of file sharing via InterPlanetary File System (IPFS) infrastructure – to spread their phishing content.

Our statistics show that the most frequently targeted brand on IPFS is Microsoft, which currently accounts for up to 20% of blocked attacks. At the same time, we see that these threats were most visible at the end of Q1/2024.
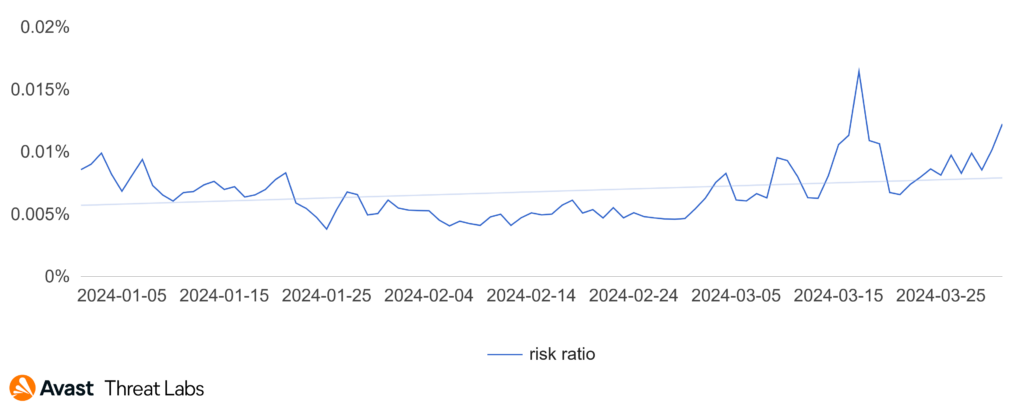

One of the most interesting phishing campaigns for this quarter was the wave of Russian-language phishing PDFs targeting bank users.
Based on the content of the PDF, this campaign was developed to target the customers of Tinkoff Bank, and from the data we can see that the most hits are registered in Latvia.


This campaign generated hundreds of PDF samples, with different names, while the appearance mostly stayed the same. All extracted URLs pointed to the same domain.

The main domain to which the URL is redirected is xsph[.]ru. This domain acts as a hub for many other types of malware.

A command-and-control server, such as one hosted at “the-packaging-experts[.]co.uk” could be accessed by malicious programs by abusing this event. This then redirects to “http://a0942143[.]xsph[.]ru/tin/cabinet/capcha/” and checks CAPTCHA to verify that the user is human, then potentially receives instructions or downloading additional payloads. Threat actors frequently employ this strategy to avoid being discovered by security solutions, using a genuine website as a front for criminal activity.

Alexej Savčin, Malware Analyst
Martin Chlumecký, Malware Analyst
Matěj Krčma, Malware Analyst
Prabhakaran Ravichandhiran, Malware Analyst
Mobile-Related Threats
The first quarter of 2024 brings with it several interesting developments within the mobile threat landscape. Adware has once again snuck into the PlayStore, this time in the form of a Minecraft clone game app. Meanwhile, MoqHao, a revived strain of banker, obtained the ability to auto-start on victims’ devices once installed, displaying phishing messages on the target device. We also saw GoldPickaxe target both Android and iOS users in Vietnam and Thailand, attempting to steal facial recognition biometrics that are then used in fraudulent payments.
State sponsored spyware was also brought back into focus with governments investigating the scope of its use on citizens, while Apple highlighted its threat notifications sent to victims of these sophisticated spywares.
Fake romance lures were also found, this time by VajraSpy, to entice victims into installing a spyware in India and Pakistan with the intent of extracting data and spying on their devices.
Finally, SpyLoans continue to spread on and off the PlayStore, enticing users with promises of quick cash but instead targeting them and their contacts with harassment and blackmail.
Web Threat Data within the Mobile Landscape
Over the last few quarters, we’ve started to include web threat data in our mobile threat telemetry. Scams are again at the top of the threat list in the mobile sphere, with a 61% increase in risk ratio compared to last quarter. This is followed by phishing and malvertising, both seeing a 19% increase in risk ratio. The increased prevalence of web threats has significantly reduced the risk ratio of traditional on-device malware such as adware, droppers and others.
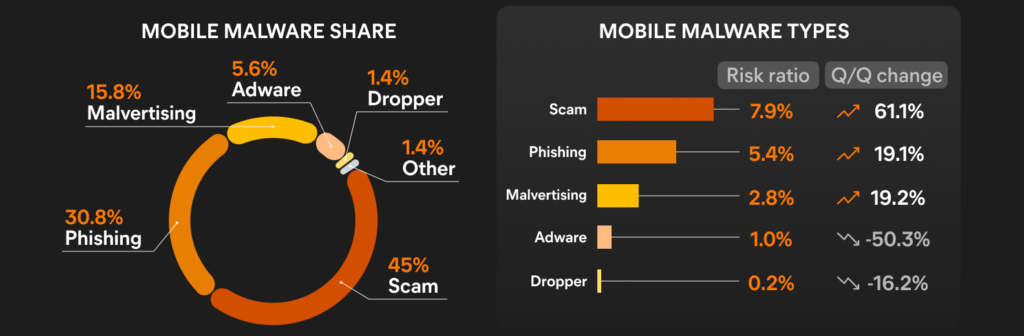
Most blocked attacks on mobile devices in Q1/2024 were web-based, mirroring the previous quarter. Users are much more likely to encounter phishing websites, scams, malvertising and other web threats than ever before. These threats can come in a variety of formats such as private messages, SMS, and emails but also redirects on less reputable sites, unwanted pop ups and through other avenues.
In contrast to these types of mobile scams, traditional on-device malware requires a more complex infection vector where the user must also install the malware. For proper functionality of most mobile malware, permissions need to be granted by the user first, which again lowers the chances of malicious activity being triggered.
Hence, blocking web-threat based attacks is beneficial for the security of mobile devices, as malware actors often use them as an entry point to get the payload onto the mobile device of their victims.
Adware Sneaks into the PlayStore Again
Adware threats on mobile phones refer to applications that display intrusive out-of-context adverts to users with the intent of gathering fraudulent advertising revenue. This malicious functionality is often delayed until sometime after installation and coupled with stealthy features such as hiding the adware app icon to prevent removal. Adware mimics popular apps such as games, camera filters, and wallpaper apps, to name a few.
Adware stays on top this quarter as the most prevalent on-device malware threat facing mobile users. Continuing to bring in fraudulent advertising revenue at the expense of the user experience of its victims, it again makes its way into the PlayStore to increase its global spread. We also observe third party stores distributing older adware families that are no longer present on the PlayStore.
HiddenAds are the most common type of adware this quarter, often hiding their icons once installed on victims’ devices or performing hidden actions in the background with the intent of gathering fraudulent ad views, unbeknownst to the victim. FakeAdBlockers and Mobidash are close behind, often masking as re-packed games that bring with them full screen out of context ads or spam notifications that bother their victims. These continue to spread through third party apps stores and malvertising on less reputable sites that redirect users to download these types of adware.

Of note this quarter is the resurgence of a previously discovered adware discussed in the Q2/2023 report, again appearing in the PlayStore with altered versions of the original adware. These Minecraft clone apps draw in millions of downloads due to the popularity of the original game, then proceed to exploit advertising SDKs to display adverts in the background, raking in ad revenue. This fraudulent activity impacts the advertising ecosystem on mobile devices and contributes to data and battery drainage on the victim’s device.
We see a significant decrease in risk ratio this quarter in mobile adware. SocialBar has mostly subsided in comparison to last quarter, accounting for the lower numbers. Alongside this, HiddenAds, FakeAdBlockers, and Mobidash have all experienced a drop in risk ratio this quarter.

Brazil, India and Argentina have the most protected users this quarter, as was the case last quarter. Egypt, Philippines and Oman have the highest risk ratios, meaning users are most likely to encounter adware in these countries, according to our telemetry.
New Auto-Starting Bankers Threaten Mobile Users
Bankers are a sophisticated type of mobile malware that targets banking details, cryptocurrency wallets, and instant payments with the intent of extracting money. Generally distributed through phishing messages or fake websites, Bankers can take over a victim’s device by abusing the accessibility service. Once installed and enabled, they often monitor 2FA SMS messages and may display fake bank overlays to steal login information.
Mobile bankers expanded their feature set in Q1/2024 with an unexpected evolution: the ability to auto-start after installation without the need for user input, as exemplified by MoqHao banker. Elsewhere, bankers are digging for gold with the new GoldPickaxe strain that targets both Android and iOS users, attempting to steal facial recognition data for further fraudulent use while emptying bank accounts. Finally, the GreenBean banker was used to redirect crypto payments by changing wallet addresses in victim’s messages. In our telemetry, we see Cerberus/Alien and BankBot with the most protected users, while RewardSteal banker makes a big splash coming in third, mainly targeting India.

We see another comeback with upgrades, as the MoqHao banker introduces the ability to auto execute after installation through using Android’s inbuilt Contact Provider service. By having this as the first activity in the app manifest with special metadata, it is executed as soon as the app is installed, enabling it to trigger malicious services before it is run for the first time by the user. Once installed and running, MoqHao starts to display phishing messages attempting to trick the user into providing their banking details. It also harvests contact details and SMS messages and sends these away to a C&C server. Interestingly, while the banker has preset country specific phishing messages, it can also dynamically load messages from Pinterest profile descriptions specifically setup for this purpose, a very odd way of delivering tailored messages to its victims. The banker has been distributed through fake phishing SMS messages, often pretending to be a delivery service and mostly targeting users in Japan, South Korea, Germany, France, and India.

GoldPickaxe, a banker targeting both Android and iOS, has emerged and is targeting victims in Thailand and Vietnam. Likely from the same threat actors behind GoldDigger, a previously discussed banker, this new strain focuses on extracting personal information and can even harvest facial recognition data for fraudulent access to victim’s bank accounts. This is likely in response to both the Bank of Thailand and the State Bank of Vietnam issuing statements advising or mandating the use of facial biometric verification for payments in the coming months.
On iOS, the threat actors initially used TestFlight, a beta testing tool within the iOS ecosystem, to distribute the iOS malware. Once Apple took down the offending banker apps, they switched to using Mobile Device Management (MDM) profiles, sending download links to victims. If the victim downloaded and installed the MDM profile, the banker would gain complete control over the device. After the complex infection process is complete, GoldPickaxe can extract photos, SMS messages and even request to capture the victim’s ID card and face. These are then used to initiate fraudulent bank payments, with reports of victims losing significant sums of money after being asked to do facial recognition scans by GoldPickaxe.
A new banker called GreenBean has been spotted spreading through a fake cryptocurrency website. Targeting users in China and Vietnam, the banker focuses on cryptocurrency wallets and payment platforms as well as traditional banking platforms. It uses the Accessibility service to gather sensitive information, login details, photos and saved wallet passwords, then sends these away to its C&C. GreenBean is also able to dynamically detect and change crypto wallet addresses it detects within messaging applications such as WeChat, redirecting a payment to its own wallet address, stealing money from victims. Additionally, the banker can stream video from the infected device, keeping an eye on its victims and potentially gaining access to sensitive information.
Breaking the trend of decline from previous quarters, bankers mostly maintain their prevalence this quarter. It is likely that the introduction of various new strains this quarter has contributed to their steadying numbers. We also observed the return of SMS and messaging applications as infection vectors, used by strains such as FluBot in the past.

Turkey has the highest risk ratio for bankers in Q1/2024. We also witnessed a notable rise in risk ratio in India, where the RewardSteal banker is gaining ground. It appears the focus this quarter has shifted towards Asia, with countries such South Korea, Japan, Thailand and Vietnam being the targets of several new strains of bankers.
State Sponsored Spyware Continues to Be a Sophisticated Threat
Spyware is used to spy on unsuspecting victims with the intent of extracting personal information such as messages, photos, location, or login details. It uses fake adverts, phishing messages, and modifications of popular applications to spread and harvest user information. State backed commercial spyware is becoming more prevalent and is used to target individuals with 0-day exploits.
Mirroring last quarter, Spymax is the most prevalent strain of spyware this quarter, followed by RealRAT, SexInfoSteal, and malicious WAMods. We also saw a few new spyware entries this quarter alongside the return of updated existing strains. Of note are official Apple threat notifications sent to affected users with iOS devices, alerting them when they have been targeted by state sponsored sophisticated spyware attacks. We see VajraSpy spreading in the PlayStore, targeting victims in Pakistan with the ability to steal sensitive data. DogeRAT, a repurposed RainbowRAT clone, makes another entrance on Github with updated and paid features. Finally, SpyLoans continue their blackmailing streak on and off the PlayStore, threatening users worldwide.
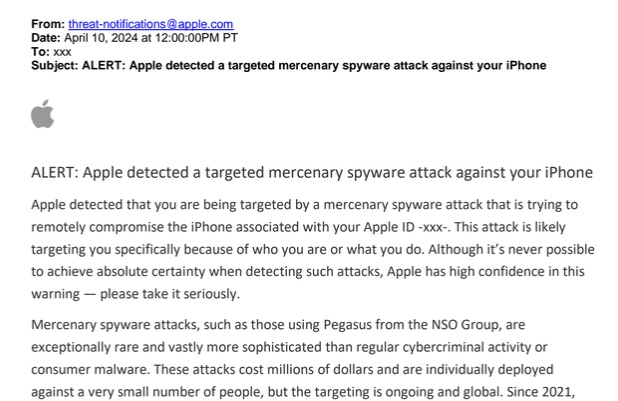
News of state sponsored spyware has been doing the rounds for at least a decade now, with examples such as the infamous NSO Group Pegasus dating back to 2016, discussed in the Q3/2021 report. Since 2021, Apple has started issuing threat notifications to potential victims, alerting them if they have been targeted by what Apple believes to be state sponsored or mercenary spyware. These attacks are often highly sophisticated, sometimes using multiple zero-day exploits to break into iOS devices without user interaction, with the intent of spying on their victims and extracting personal information such as SMS messages, contacts and photos. There has been more focus on the use of such spyware by governments, with Poland recently launching a probe into the use of Pegasus by the government, which allegedly targeted close to 600 individuals in Poland. Due to the high cost of such attacks, the attackers are targeting only individuals of interest, NGOs, etc. Users should take extra precautions, such as enabling Lockdown mode on iOS devices and keeping their device up to date with latest security updates.

VajraSpy, an upgraded spyware seen in previous years, has made it onto the PlayStore, targeting users in India and Pakistan. Masquerading as messaging and dating apps, victims were likely approached under the guise of a romantic encounter, where threat actors encouraged victims to download the spyware apps to continue their interaction. It appears there were three distinct versions of the malware, two of which were messaging applications with the ability to extract SMS messages, WhatsApp conversations and photos, the more advanced version even able to record audio and video, log keystrokes, and listen in on phone calls. The third version disguised itself as a news app and didn’t request any dangerous permissions. Despite this, it was able to steal contacts and various documents and files from external storage.

Github is again being used for distribution of potential malware in this case DogeRAT. This update appears to be a repurposed version of RainbowRAT, and even features a paid version that promises to be undetectable by antivirus in addition to having the ability to extract all photos on a device, screenshot the victim’s screen and provide a keylogger to track inputs. While dangerous, open repositories such as this one offer an interesting insight into the operation of various threat actors. Normally, threat groups try to hide their activity to evade detection and remain under the radar for as long as possible to avoid takedowns and antivirus detection.

SpyLoans continue to reign on the PlayStore, targeting victims in need of quick cash with promises of easy payments, low interest rates and hassle-free setup. Numerous apps have been taken down from the PlayStore, as discussed in previous quarters, but new ones keep popping up. The actors behind these apps have also taken to using third party app stores or even direct messaging to entice victims into downloading their malware. Once installed, the SpyLoans generally harvest contacts, photos and SMS messages under the guise of a credit check. This data is then used to harass and blackmail victims, in some cases even threating violence. Users are advised to stick to official banks when in need of a loan, to avoid SpyLoan apps.

The risk ratio for mobile spyware has remained steady compared to Q4/2023, with a very slight decrease in prevalence of spyware in our telemetry. The continued spread of SpyLoans may have contributed to this.

Yemen has the highest risk ratio this quarter, followed by Turkey, Egypt and Pakistan. We saw VajraSpy mainly focus on Pakistan this quarter, where we do see an increase in risk ratio. Brazil and the US have the highest number of protected users.
Jakub Vávra, Malware Analyst
Malware researchers
Adolf Středa
Alexej Savčin
David Álvarez
David Jursa
Igor Morgenstern
Jakub Křoustek
Jakub Vávra
Jan Rubín
Jan Vojtěšek
Ladislav Zezula
Luigino Camastra
Luis Corrons
Martin Chlumecký
Matěj Krčma
Michal Salát
Ondřej Mokoš
Prabhakaran Ravichandhiran
Vladimír Žalud
Data analysts
Pavol Plaskoň
Filip Husák
Lukáš Zobal
Communications
Brittany Posey
Nyrmah Reina Terreforte
The post Avast Q1/2024 Threat Report appeared first on Avast Threat Labs.
