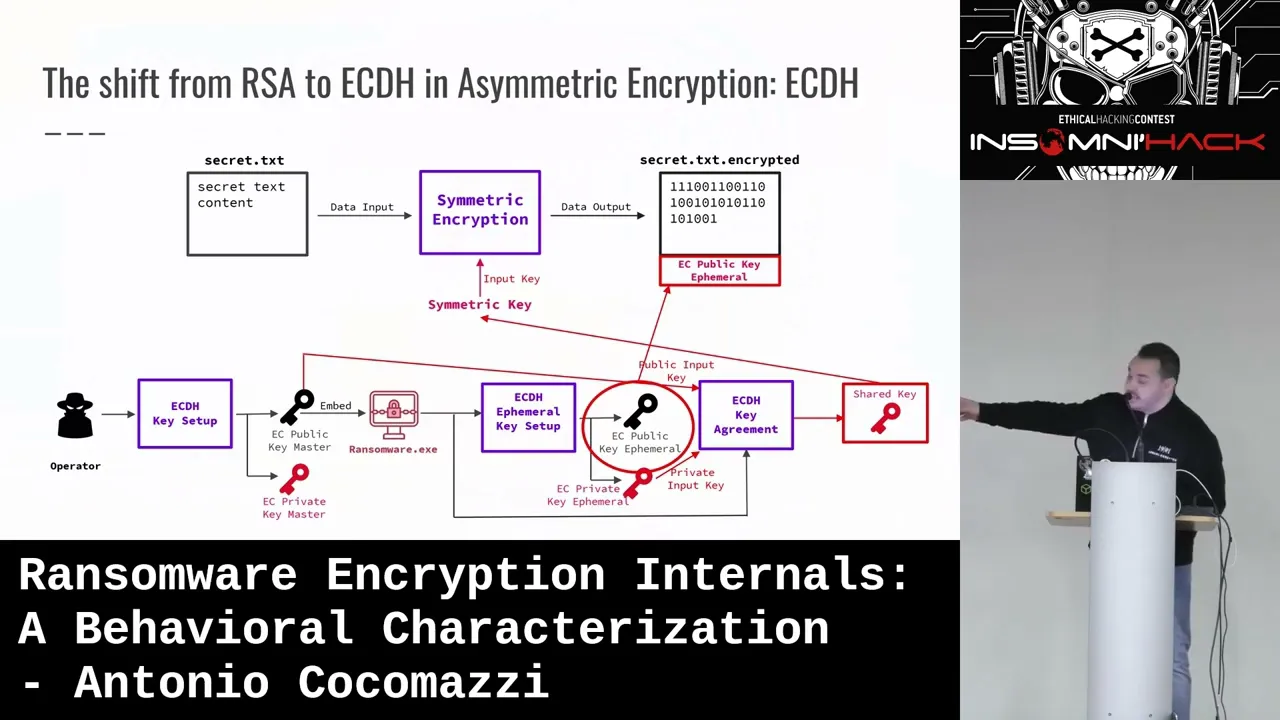
Reading view
No more JuicyPotato? Old story, welcome RoguePotato!

by splinter_code & decoder_it - 11 May 2020 After the hype we ( @splinter_code and me) created with our recent tweet , it’s time t...
Locky Ransomware is back! 49 domains compromised!

by splinter_code - 26 June 2016 Locky ransomware starts up again its illegal activity of stealing money from their victims after a temporary inactivity since the end of May. This time, it comes with hard-coded javascript...
New Locky variant – Zepto Ransomware Appears On The Scene
by splinter_code - 7 July 2016 New threat dubbed Zepto Ransomware is spreading out with a new email spam campaign. It is a variant of the...
Reverse Engineering a JavaScript Obfuscated Dropper

by splinter_code - 31 July 2017 1. Introduction Nowadays one of the techniques most used to spread malware on windows systems is...
Weaponizing Mapping Injection with Instrumentation Callback for stealthier process injection

by splinter_code - 16 July 2020 Process Injection is a technique to hide code behind benign and/or system processes. This technique is u...
RomHack2020 - Windows Privilege Escalations: Still abusing local service accounts to get SYSTEM privileges
Slides here: https://github.com/antonioCoco/infosec-talks/blob/main/RomHack2020_Windows_Privilege_Escalations_Still_abusing_Service_Acco...
Relaying Potatoes: Another Unexpected Privilege Escalation Vulnerability in Windows RPC Protocol

by splinter_code & decoder_it - 26 April 2021 Executive Summary Every Windows system is vulnerable to a particular NTLM relay attack...
We thought they were potatoes but they were beans (from Service Account to SYSTEM again)
by splinter_code - 6 December 2019 This post has been written by me and two friends: @splinter_code and 0xea31 This is the “unintended...